In the past, I’ve made a few one-off PowerShell scripts to set various registry settings. I find myself needing to do this more and more. I’ve always just forced my registry settings with no regard to whether the settings were already correct.
A perfect example of this is my PowerShell script to Disable Auto Windows Updates
While this method works I felt like it could be better. I decided to make a brand new script that would be less forceful and more modular and use functions and parameters.
This resulted in the creation of the PowerShell script that I call the Registry Check Setter.
The PowerShell script enables you to set multiple registry settings very easily while checking if the settings are already correct or not.
You can find the script on my GitHub https://github.com/thedxt/Registry-Check-Setter
How It Works
The script starts by checking if the registry key path exists, if the key path doesn’t exist the script considers it safe to just set the settings and sets them. If the key path does exist the script then moves on to checking if the registry value name exists.
If the registry value name is not found in the registry key path the script then creates the value with the needed setting and exists. If the registry value name exists the script then checks if the registry value name setting is correct.
If the registry value name setting is not correct the script then changes the setting to make it correct and then exits.
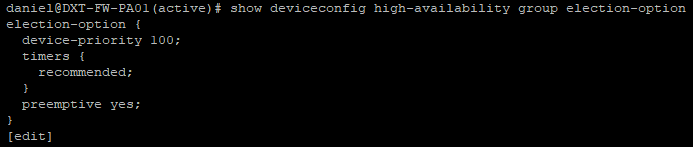
An example of this would be if I was trying to prevent a Windows 10 system from upgrading to Windows 11 and I wanted to turn off auto updates.
To lock the system to Windows 10 the registry path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate needs a registry value named ProductVersion that is a String with a setting of Windows 10.
To lock the system to a specific feature update of Windows 10 the registry path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate needs a registry value named TargetReleaseVersionInfo that is a String with a setting of 22H2.
To enable locking the system to Windows 10 22H2 the registry path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate needs a registry value named TargetReleaseVersion that is a DWord with a setting of 1.
To turn off auto updates the registry path HKLM:\SOFTWARE\Policies\Microsoft\Windows\WindowsUpdate\AU needs a registry value named NoAutoUpdate that is a DWord with a setting of 1.
Yes, I could just force the settings to be correct but if I run the script multiple times it constantly changes the settings and doesn’t take into account if the Windows Update service is running. If the Windows Update service is already running these settings won’t properly take effect until the Windows Update service is restarted or the whole system is rebooted.
My thought process is you could combine the results of the Registry Check Setter to have another script take action.
…