Palo Alto Private Data Reset with HA (Active/Passive)

Sometimes, you need to do a quick factory reset on a Palo Alto Networks firewall. If you aren’t decommissioning the firewall, a Private Data Reset can be a faster way to accomplish similar results as a factory reset and can be done via CLI directly and could technically be done remotely with some coordination.
In this post, I will show you step-by-step instructions on how to perform a private data reset on a primary Palo Alto Networks firewall in an Active/Passive High Availability Pair using the GUI and the CLI.
The Process
- Confirm local firewall admin access
- Confirm management network access
- Disable HA Preemptive Election via the GUI or CLI
- Export the running config via the GUI or CLI
- Make the primary firewall the Passive firewall via the GUI or CLI
- Perform the Private Data Reset
- Perform the initial configuration of the reset firewall
- Import the exported running config
- Resolve High Availability issues
- Sync the High Availability Running Config via the GUI or CLI
- Test High Availability via the GUI or CLI
- Enable HA Preemptive Election via the GUI or CLI
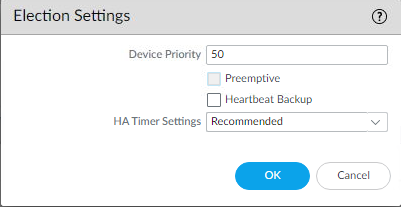
HA Election Settings
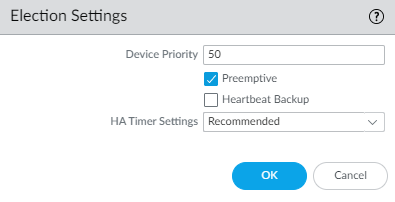
If the HA election settings are set to preemptive, we need to disable that.
HA Election Settings GUI
- On the Primary firewall, click on Device.
- Click on High Availability
- Uncheck Preemptive (if it isn’t selected, you don’t need to do anything)
- Commit the changes
HA Election Settings CLI
- SSH into the Primary firewall
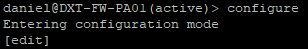
- Enter the configuration mode by running the command
configure
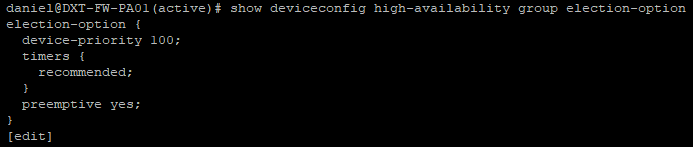
- Run the following command to output your HA election settings
show deviceconfig high-availability group election-option
If preemptive is set to yes, make a note of that (if it isn’t selected, you don’t need to do anything)
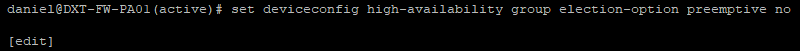
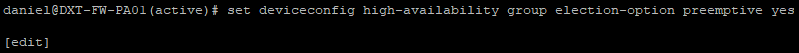
- Run the following command to disable the HA preemptive election
set deviceconfig high-availability group election-option preemptive no
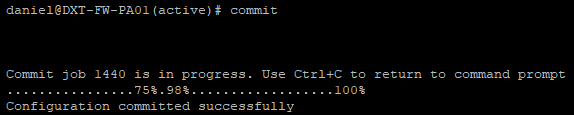
- Run the following command to save the changes
commit
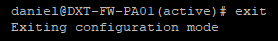
- Exit configuration mode by running the command
exit
Export Running Config
We need to export the running config to reimport it after the Private Data Reset.
Export Running Config GUI
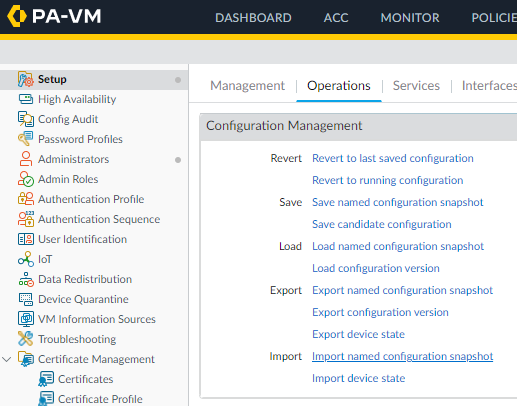
- Click on Setup
- Click on Operations
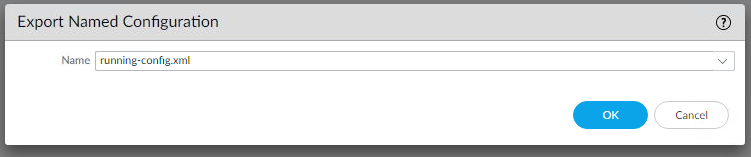
- Click on Export named configuration snapshot.
- Select running-config.xml
Export Running Config CLI
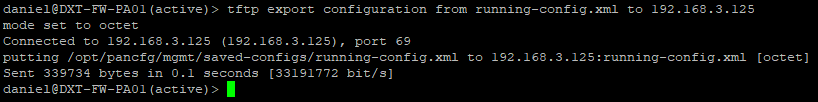
- Run the following command to export the running config, replace TFTP_IP with the IP of your TFTP server
tftp export configuration from running-config.xml to TFTP_IP
For me, that command will look like tftp export configuration from running-config.xml to 192.168.3.125
Suspend HA on the Active Firewall
We need to move traffic off the active firewall to the passive firewall. To do this, we need to suspend High Availability on the active firewall, which will force a failover to the passive firewall.
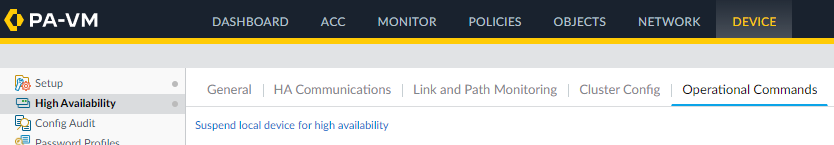
Suspend HA on the Active Firewall GUI
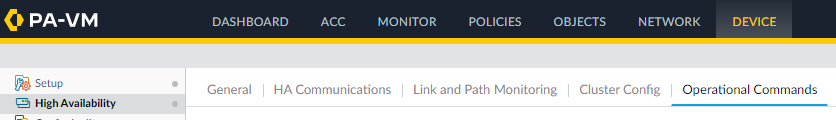
- Click on High Availability
- Click on Operational Commands
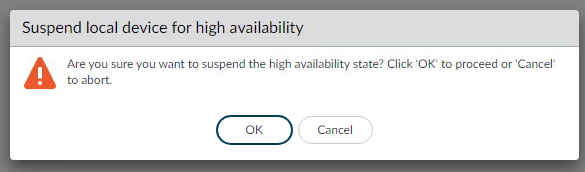
- Click on Suspend local device for high availability.
- Click OK
We should now be failed over to the secondary firewall.
- Click on Dashboard
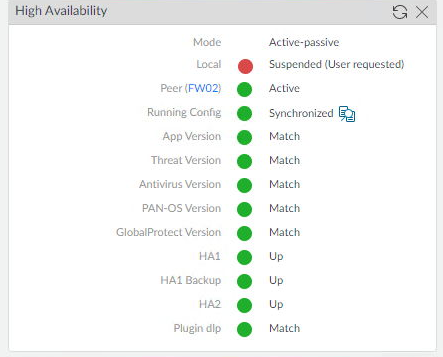
- Confirm that the local status says Suspended and the Peer status says Active.
- Confirm that traffic is still working to confirm that your failover worked.
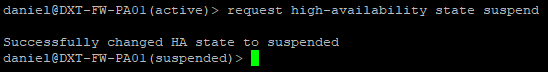
Suspend HA on the Active Firewall CLI
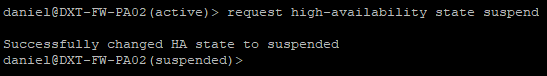
- Run the following command to suspend HA on the currently Active firewall
request high-availability state suspend
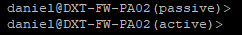
- Confirm that your secondary firewall is now active by logging into it. It should no longer say passive in SSH. If you are already logged into SSH on the secondary firewall, press enter, and it should switch.
- Confirm that traffic is still working to confirm that your failover worked.
Private Data Reset
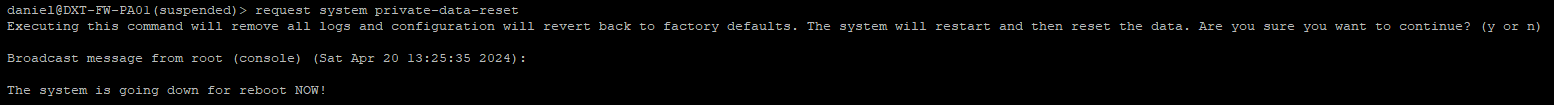
- SSH into the suspended firewall
- Enter the following command to perform the private data reset
request system private-data-reset
- Confirm that the firewall will be reset back to factory defaults and rebooted by pressing y
The firewall will now reboot and preform the Private Data Reset. Once completed the Palo Alto firewall will boot up in the default configuration, all logs and configs will be reset.
- While you wait rename the exported running-config.xml to something else as it will need a different name before we can import it. I called mine B4_reset-running-config.xml.
Initial config
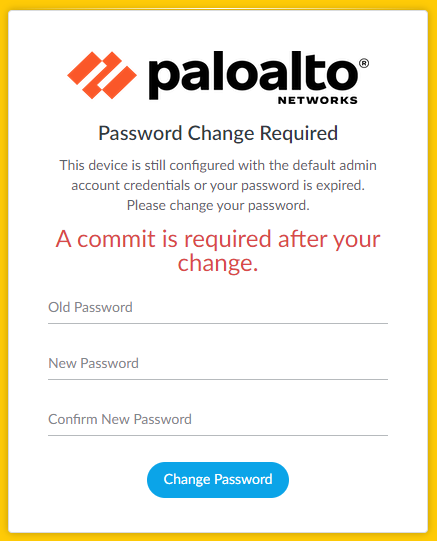
Once the firewall has booted up, the admin credentials will be the default of admin for the username and admin for the password.
- Log in to the freshly reset Palo Alto firewall.
- Change the default password.
- Log in again with the new password.
Import the Exported Config
- Click on Device
- Click on Setup
- Click on Operations
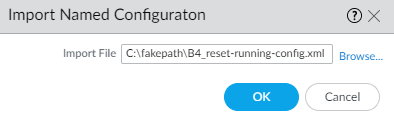
- Click on Import named configuration snapshot.
- Select the exported running config you exported and renamed earlier. Mine is called B4_Reset-running-config.xml.
- Click Close
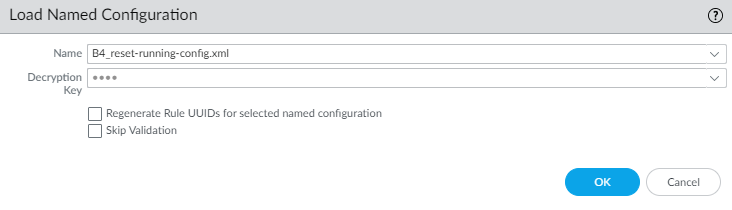
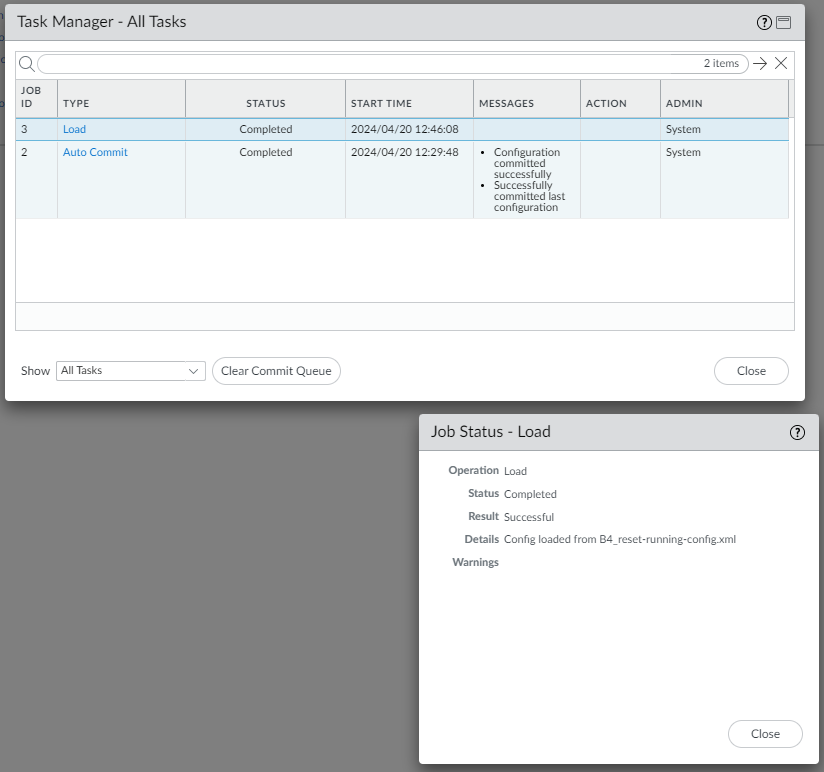
- Click Load named configuration snapshot.
- Select the config you imported. Mine is called B4_Reset-running-config.xml.
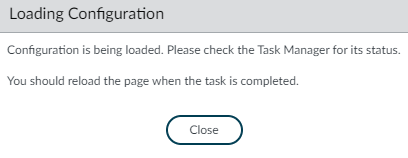
- Click Close
- Once the task is completed, refresh the page.
- Commit your changes
High Availability Config
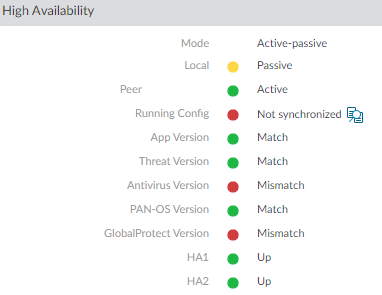
- Resolve your HA conflicts. In my case, I needed to resolve the Antivirus Version and the GlobalProtect Version.
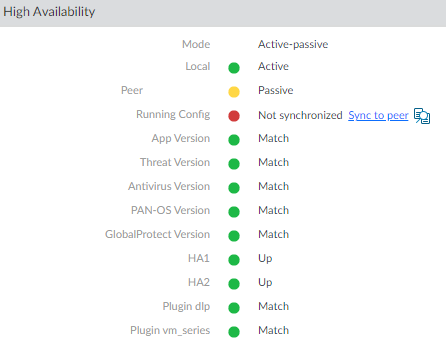
Running Config Sync GUI
- Log in to your secondary firewall that is currently active.
- Click Sync to peer.
- Click Yes to confirm that you will overwrite the peer configurations.
Running Config Sync CLI
- SSH into the secondary firewall that is currently active.
- Enter the following command to sync the config
request high-availability sync-to-remote running-config
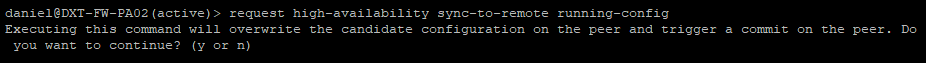
- Confirm that you want to continue by pressing y
Test High Availability
As we just reset one of the firewalls, we should test the High Availability.
Test HA GUI
- Login to your secondary firewall that is currently active.
- Click on Device
- Click on High Availability
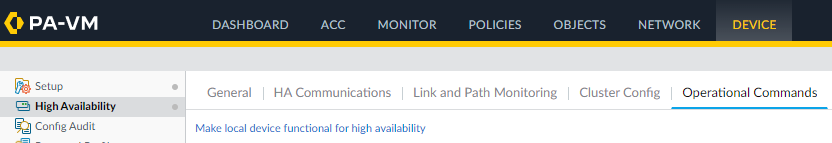
- Click on Operational Commands
- Click on Suspend local device for high availability.
- Click OK
We should now be failed over to the Primary firewall.
- Confirm that traffic is still working to confirm that your failover worked.
- Click Make local device functional for high availability to make the secondary firewall available for HA again.
Test HA CLI
- SSH into the secondary firewall that is currently active.
- Run the following command to suspend HA on the currently Active firewall
request high-availability state suspend
We should now be failed over to the Primary firewall.
- Confirm that traffic is still working to confirm that your failover worked.
- Run the following command to make the secondary firewall available for HA again
request high-availability state functional
Enable HA Election
If you disabled HA election, we need to turn that back on.
HA Election GUI
- Log in to the primary firewall
- Click on Device
- Click on High Availability
- Check Preemptive
- Commit the changes
HA Election CLI
- SSH into the primary firewall
- Enter the configuration mode by running the command
configure
- Run the following command to enable the HA preemptive election
set deviceconfig high-availability group election-option preemptive yes
- Run the following command to save the changes
commit
- Exit configuration mode by running the command
exit
Closing
That is all it takes to perform a private data reset on the primary Palo Alto Networks firewall in an Active/Passive High Availability Pair using the GUI and the CLI.
If you want to read more about the private data reset, here is a Palo Alto Knowledge Base Article about it.
If your firewall was impacted by the Level 2 Compromise of CVE-2024-3400 the Private Data Reset will wipe out any lingering items. For direction on CVE-2024-3400, please reach out to Palo Alto Networks Support and see the Palo Alto Security Advisory for CVE-2024-3400.


















Leave a comment