Update
The process detailed below works perfectly on Windows 11 however, on Windows 10 the process below will lock the Start Menu layout preventing users from being able to pin anything to the Windows 10 Start Menu or change anything in the Start Menu. The process to fix this is to also deploy a default Windows 10 Start Menu the process for the fix is detailed in my post Intune Deploy Windows 10 Default Start Menu.
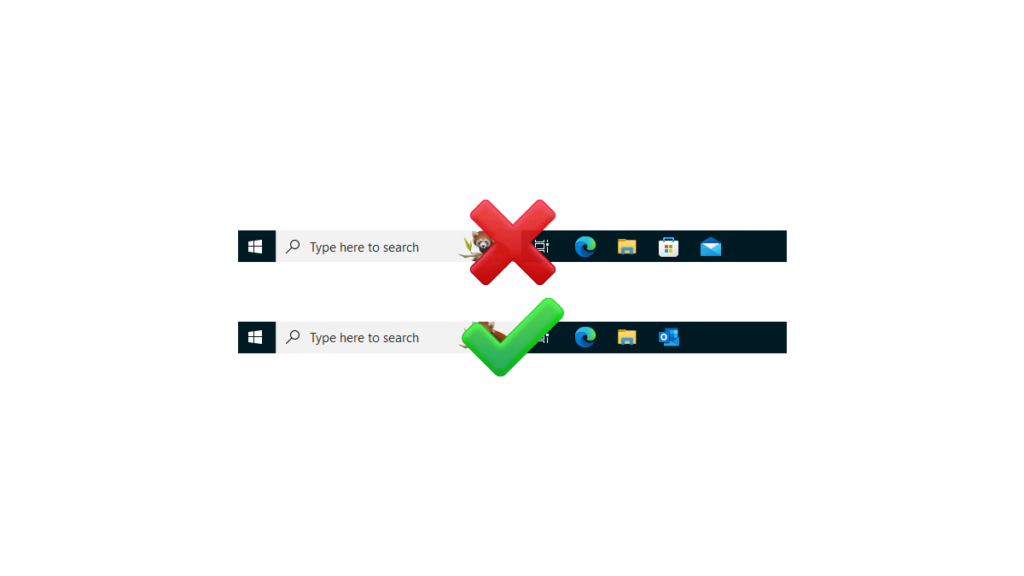
Deploying the same taskbar to all users is a very nice quality of life improvement, as it can help eliminate the problems of users using Windows Mail instead of the already installed Microsoft Outlook.
I opted to deploy a standard default taskbar using Microsoft Intune as Microsoft Office is a required application on all Intune systems in my setup so I didn’t need to worry about a system trying to pin Microsoft Outlook when it wasn’t installed.
In this post, I’ll show you step-by-step how to create the taskbar XML file and how to deploy it to Windows 10 and Windows 11 using Microsoft Intune.
Create the XML
<?xml version="1.0" encoding="utf-8"?>
<LayoutModificationTemplate
xmlns="http://schemas.microsoft.com/Start/2014/LayoutModification"
xmlns:defaultlayout="http://schemas.microsoft.com/Start/2014/FullDefaultLayout"
xmlns:start="http://schemas.microsoft.com/Start/2014/StartLayout"
xmlns:taskbar="http://schemas.microsoft.com/Start/2014/TaskbarLayout"
Version="1">
<CustomTaskbarLayoutCollection>
<defaultlayout:TaskbarLayout>
<taskbar:TaskbarPinList>
<taskbar:UWA AppUserModelID="Microsoft.MicrosoftEdge_8wekyb3d8bbwe!MicrosoftEdge" />
<taskbar:DesktopApp DesktopApplicationLinkPath="%APPDATA%\Microsoft\Windows\Start Menu\Programs\System Tools\File Explorer.lnk" />
</taskbar:TaskbarPinList>
</defaultlayout:TaskbarLayout>
</CustomTaskbarLayoutCollection>
</LayoutModificationTemplate>
Code language: HTML, XML (xml)
We will need to make some changes as it isn’t perfect. We will start by telling Windows to unpin all the default pinned apps.
- To remove all the default pinned apps we need to change
<CustomTaskbarLayoutCollection> to be <CustomTaskbarLayoutCollection PinListPlacement="Replace">
Even though we configure the taskbar XML to replace the default pinned apps this has no impact on the apps the user has pinned, it may move the items to the start of the taskbar if they have them pinned further down but that’s it.
Now we can start adding the pinned apps we want. I like to set them in the following order Microsoft Edge, File Explorer, then Microsoft Outlook.
- To pin Microsoft Edge I’m going to replace
<taskbar:UWA AppUserModelID="Microsoft.MicrosoftEdge_8wekyb3d8bbwe!MicrosoftEdge" /> with <taskbar:DesktopApp DesktopApplicationLinkPath="%ALLUSERSPROFILE%\Microsoft\Windows\Start Menu\Programs\Microsoft Edge.lnk"/> As I didn’t want to use the UWA method as I tend to trust file paths more but in theory you could skip this part.
…