Securing GlobalProtect

Out of the box, you can’t just add a Security Profile to the interface that runs GlobalProtect fortunately there’s a relatively easy way to do it with minimal impact to your existing GlobalProtect setup.
In this post, I will show you step-by-step how to secure GlobalProtect by adding protection with a Vulnerability Protection Profile or a Security Profile Group to an already existing GlobalProtect setup by using a loopback interface.
The Process
- Log in to the Palo Alto Networks Firewall
- Click on Objects
- Click on Addresses
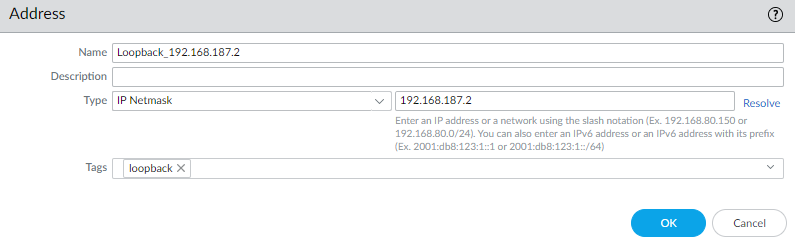
- Add a new address for your loopback address
I will be using the address 192.168.187.2 for this example.
- Click on Network
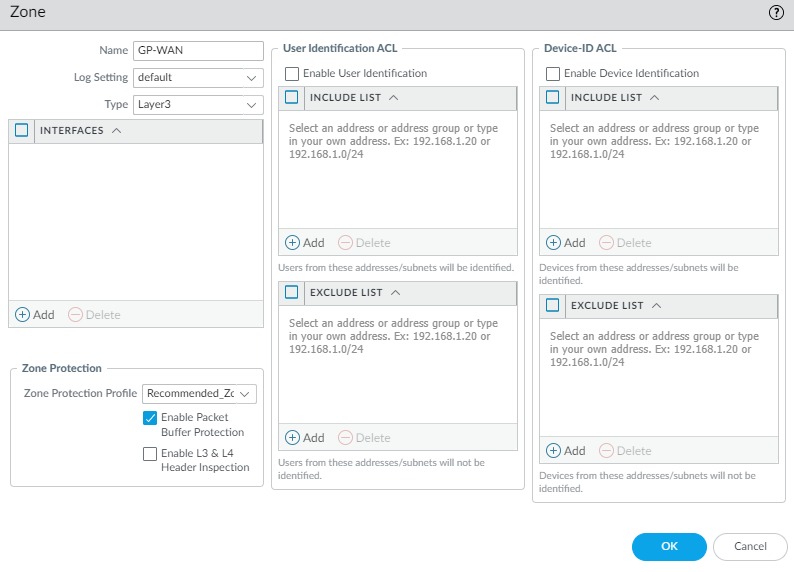
- Click on Zones
- Add a new Zone. I will be using the name GP-WAN. (This zone will be the zone allocated to the GlobalProtect loopback interface later on.)
- Set the Type to Layer3
- Select your Zone Protection Profile. In my case, I will use the one called Recommended_Zone_Protection
- Select the option to Enable Packet Buffer Protection.
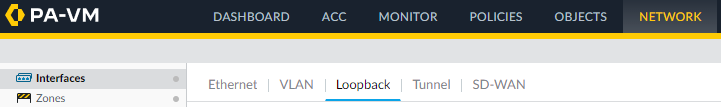
- Click on Interfaces
- Click on Loopback
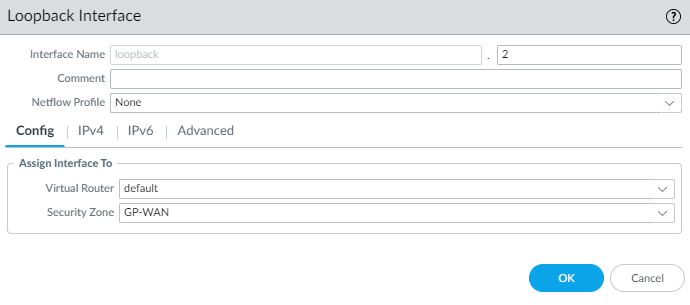
- Add a new loopback interface.
- Enter a number for your loopback interface I will be using number 2.
- Set the Virtual Router. I will be using the virtual router named default.
- Set the Security Zone to the one you created earlier. I will be using the security zone named GP-WAN.
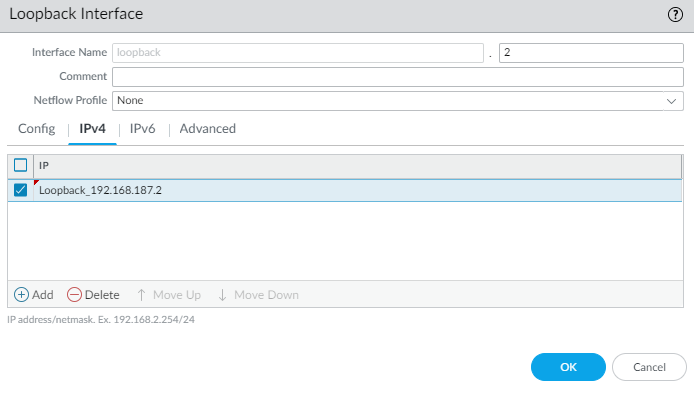
- Click on IPv4 and add the loopback address object you created earlier.
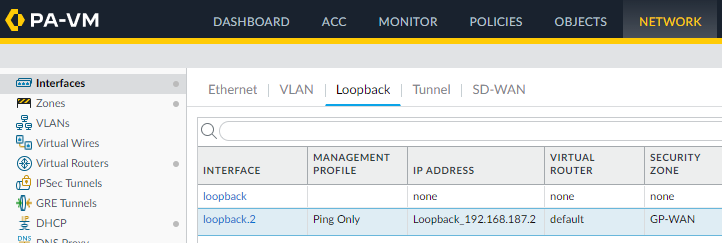
It should look something like this once completed.
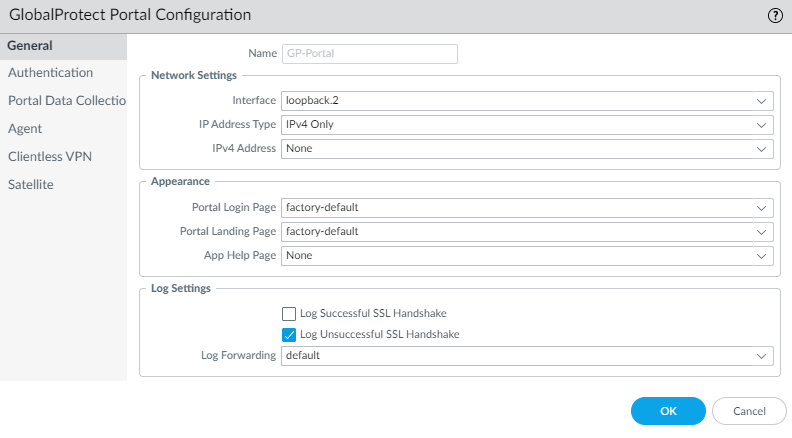
- Click on GlobalProtect > Portals
- Select your GlobalProtect Portal and change the interface to the loopback interface
In my setup that is loopback.2
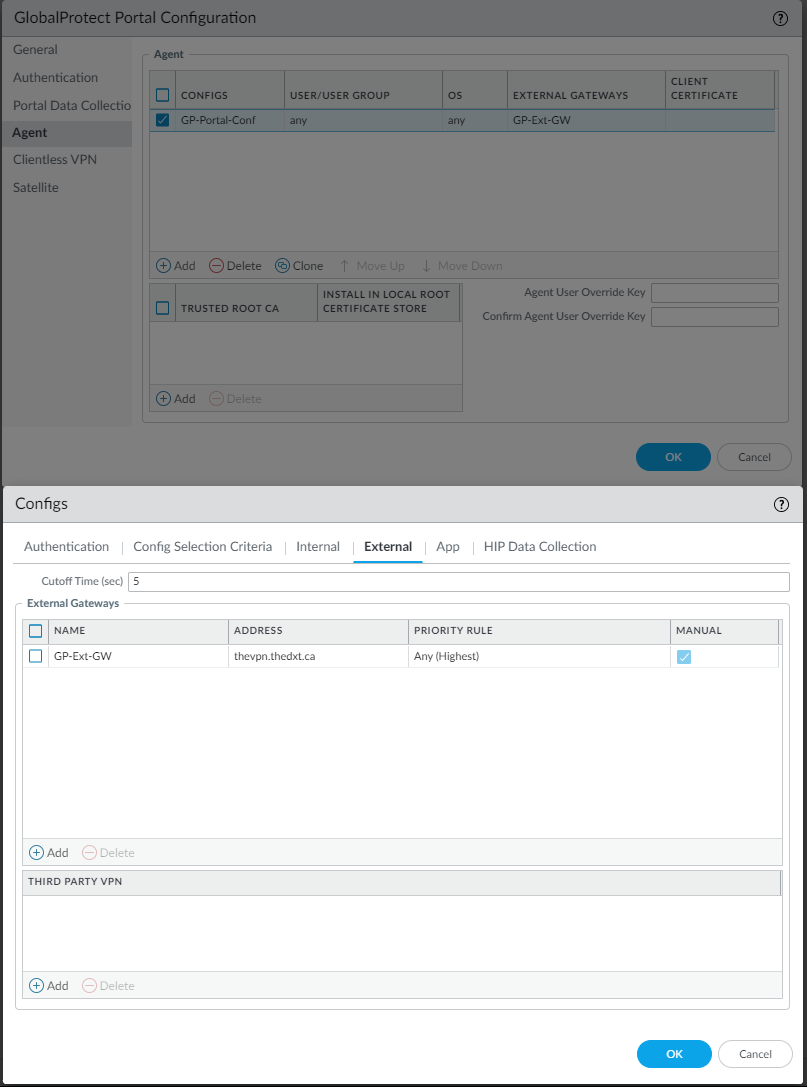
Depending on your settings you may also need to update the GlobalProtect Portal Agent Config External Gateway address. In my case, I am using the external FQDN so I don’t need to change anything.
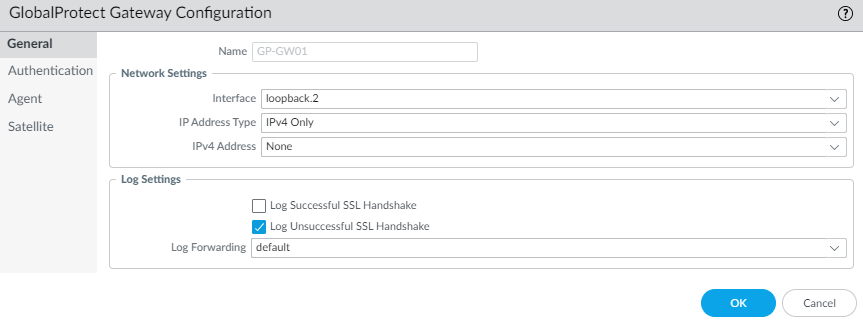
- Click on GlobalProtect > Gateways
- Select your GlobalProtect Gateway and change the interface to the loopback interface.
In my setup that is loopback.2
- Click on Policies
- Click on NAT
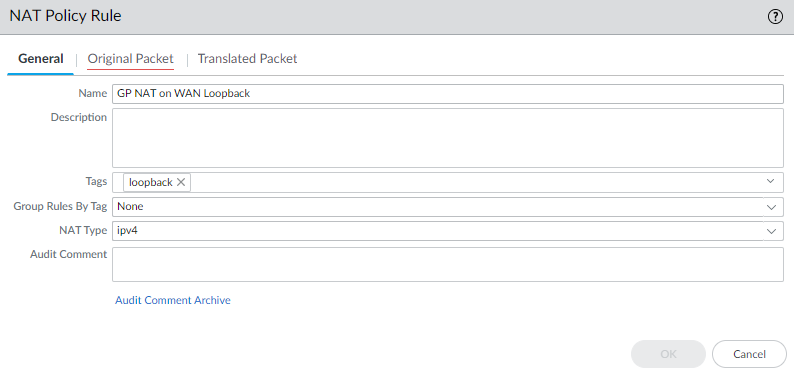
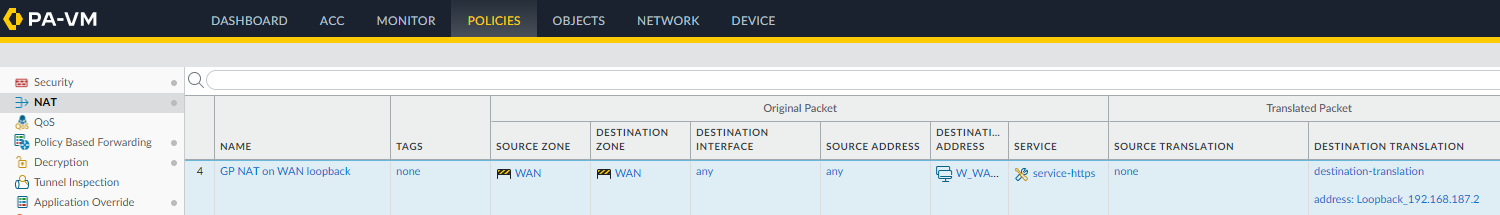
- Add a new NAT policy rule. I will call mine GP NAT on WAN loopback
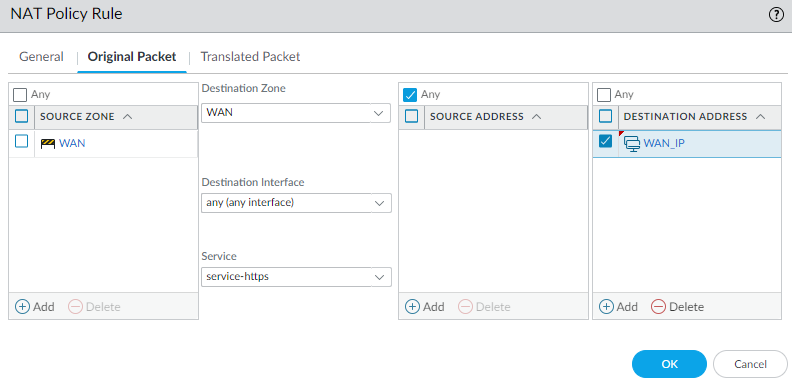
- Set your Source Zone to your external internet zone. In my setup that zone is called WAN
- Set the Destination Zone to the same zone as the source zone
- Set the Destination Address to the IP of the external interface that handles GlobalProtect, not the loopback address. In my setup, I have an address object called WAN_IP which is the external IP that I will be using for GlobalProtect.
- Set the Service to service-https
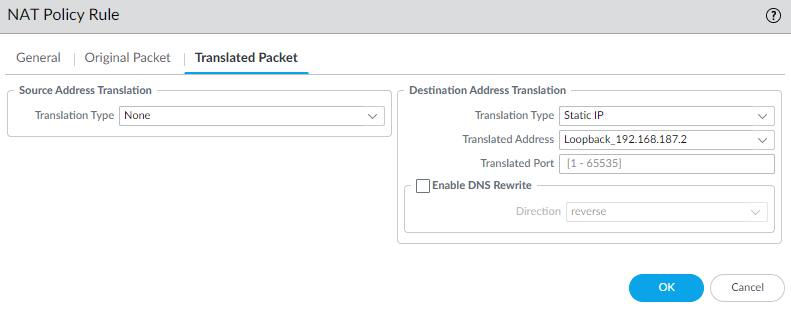
- For Translated Packet set the Destination Address Translation to the following
- Set Translation Type to Static IP
- Set the Translated Address to the Loopback Address Object for the GlobalProtect interface that we created earlier.
The NAT policy rule should look something like this.
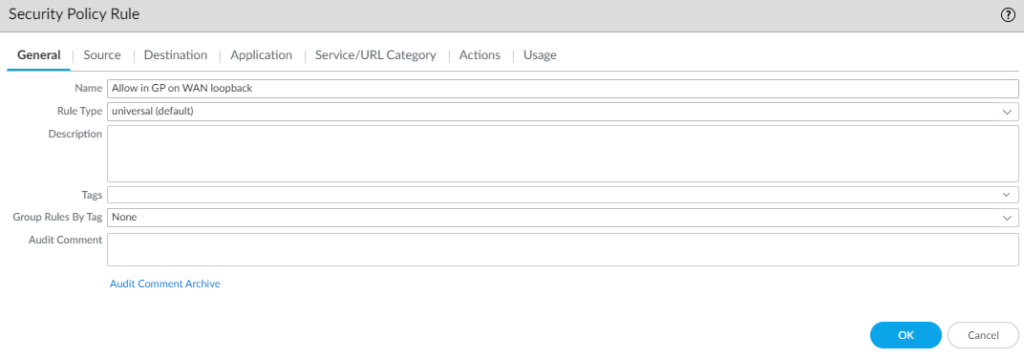
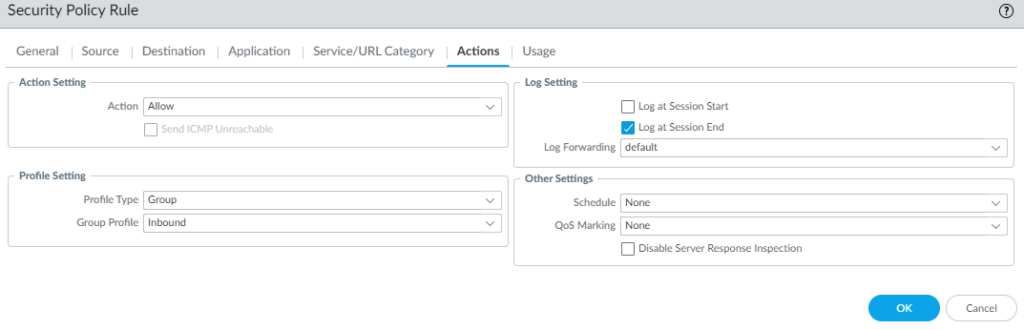
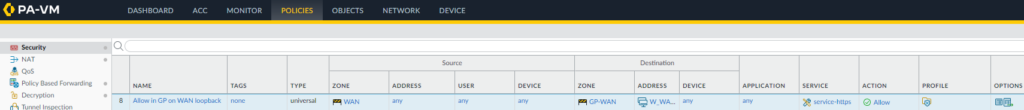
- Click on Security
- Add a new security policy rule. I will call mine Allow in GP on WAN loopback.
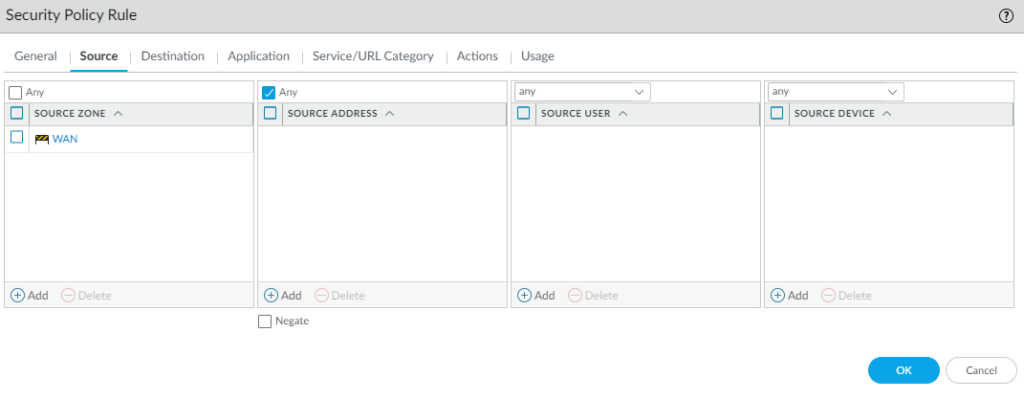
- Set your Source Zone to your external internet zone. In my setup that zone is called WAN.
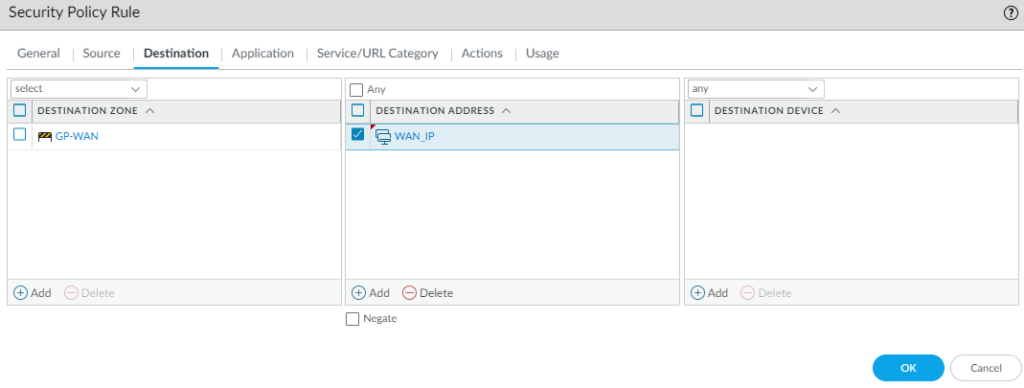
- Set the Destination Zone to the zone you used for the GlobalProtect Loopback interface. In my setup that is a zone called GP-WAN.
- Set the Destination Address to the IP of the external interface that handles GlobalProtect, not the loopback address. In my setup, I have an address object called WAN_IP which is the external IP that I will be using for GlobalProtect.
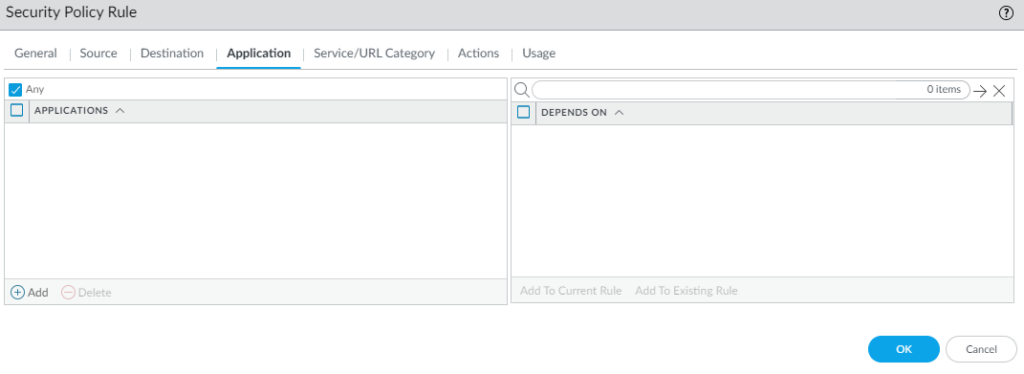
- Set Applications to Any
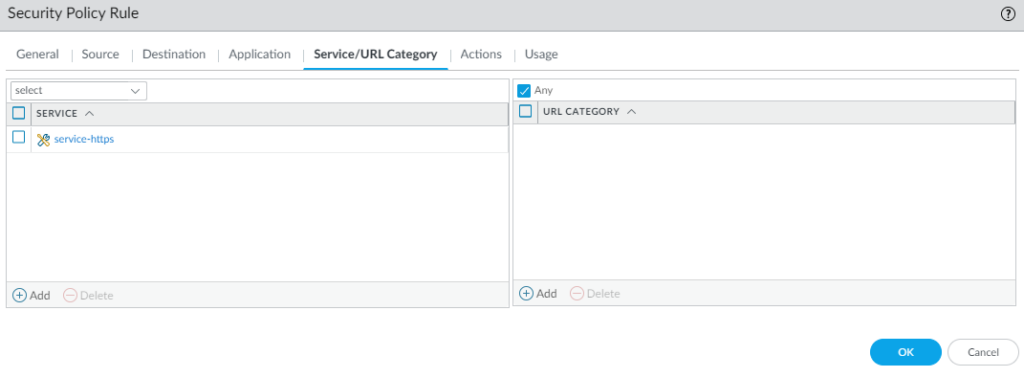
- Set the Service/URL Category to the service service-https
- Set the Actions for Profile Setting to a group that includes a vulnerability protection profile or just select vulnerability protection profile.
I will be using the Security Profile Group I already have called Inbound which includes a vulnerability protection profile.
The Security policy rule should look something like this
- Commit your changes.
You now have GlobalProtect still running on 443 but using a NAT policy rule to send it to the loopback interface and a security policy rule to add vulnerability and other protections to the GlobalProtect interface.
If you are protecting against CVE-2024-3400 you may need to make changes to your Vulnerability Protection Profile to include Threat IDs 95187, 95189, and 95191. For more information see the Palo Alto Security Advisory for CVE-2024-3400.
This process can help mitigate CVE-2024-3400 for more information and direction from Palo Alto Networks for the vulnerability here is the Palo Alto Security Advisory for CVE-2024-3400.










2 responses to “Securing GlobalProtect”
nice article but it’sn’t the CVE 2024 3440 !!! ==> CVE-2024-3400
thank you. Oops yes you are correct I made a typo. That’s fixed now. Thanks for the heads up.