FortiGate Hair-pinning
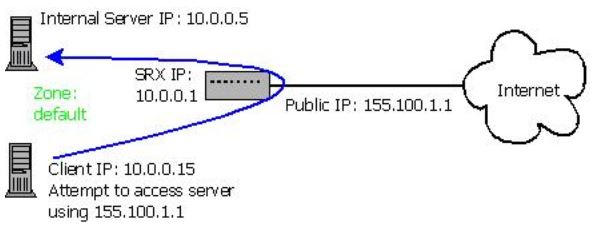
I have been playing around with Policy mode on the FortiGate and an issue that I’ve ran into a few times is if you have something hosted internally that also needs to be accessed externally it doesn’t work internally when you use the external address, for example a reverse proxy.
In my setup I use a reverse proxy in front of my WordPress Docker containers. Due to this they are running on random ports. When I need to access them I need to use the external address not the LAN address. A half workaround that I was doing, was using CloudFlare proxied mode which did work but I wanted to fix it without needing to do that.
I was looking at my deny logs in my FortiGate I noticed that my guest network was trying to talk to one of the websites that is hosted internally, however I noticed that the destination was the WAN IP but it also had the NAT IP and it showed that the destination Interface was my LAN not my WAN.
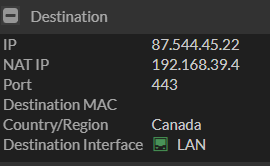
I realized that the rule I was missing in my FortiGate was a Hair Pin rule. Which makes it so that when it goes to leave the FortiGate externally it comes back but it comes back on your LAN interface so it shows up as my guest network is trying to talk to my LAN.
To correct this I made a rule that allows traffic from my Guest network to the NAT IP on my LAN to be allowed and boom problem solved.
You can read more about FortiGate Hair-pinning here https://docs.fortinet.com/document/fortigate/5.4.0/cookbook/856642/configuring-hair-pinning-on-a-fortigate








Leave a comment