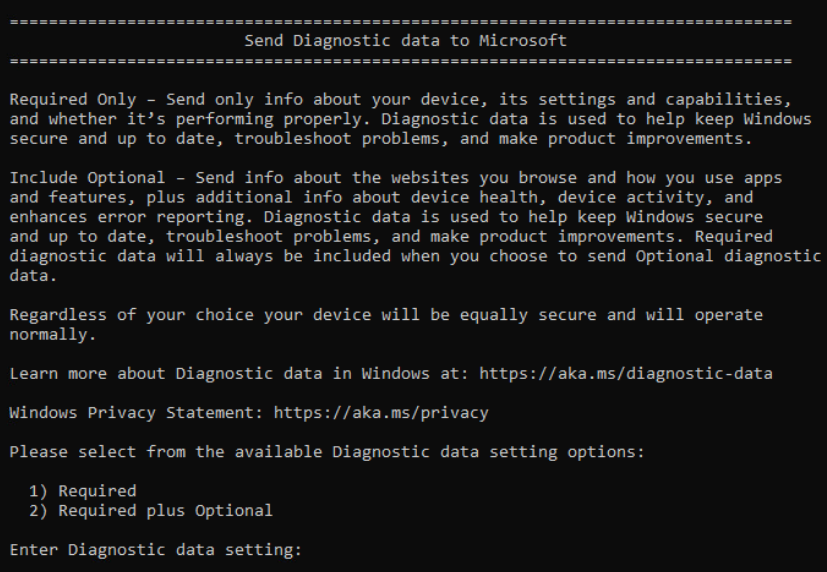
VMware vCenter Native Key Provider
VMware vCenter can be a key provider, which is perfect for using a vTPM (Virtual Trusted Platform Module). With VMware vSphere, you can configure a native key provider that VMware vCenter fully manages. No external key provider is needed. The native key can even be used to encrypt your VMs.
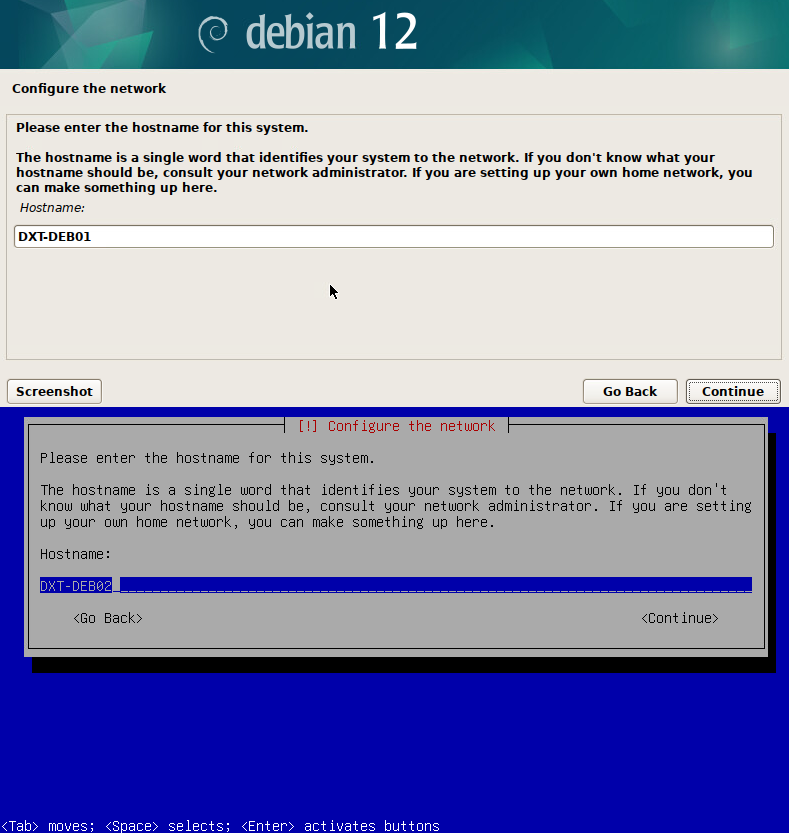
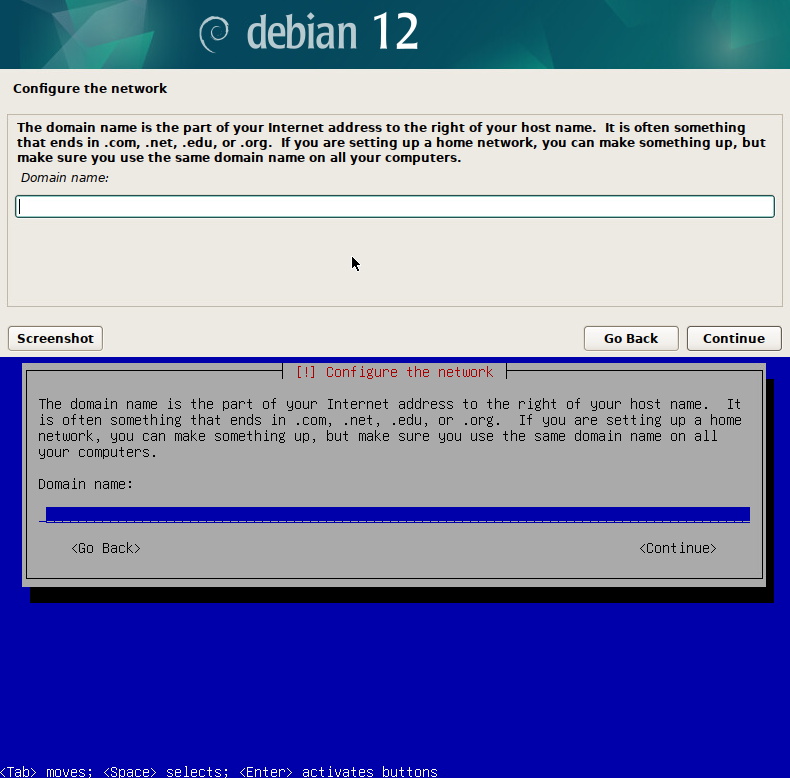
In this post, I will show you step-by-step how to add a Native Key Provider (NKP) to VMware vCenter.
The Process
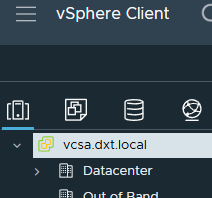
- Login to VMware vCenter.
- Click on your vCenter.
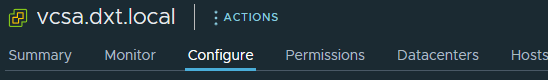
- Click on the Configure tab.
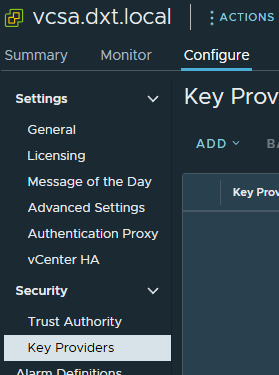
- Under the Security section, click on Key Providers.