Minisforum MS-A2 BIOS Options
Recently, I acquired a Minisforum MS-A2 system and have been experimenting with it in my home lab. Something that’s been bothering me is the lack of documentation about all the different BIOS menus. I’ve also found myself forgetting which BIOS menu I saw which option. To address my issue, I decided to document all the BIOS options.
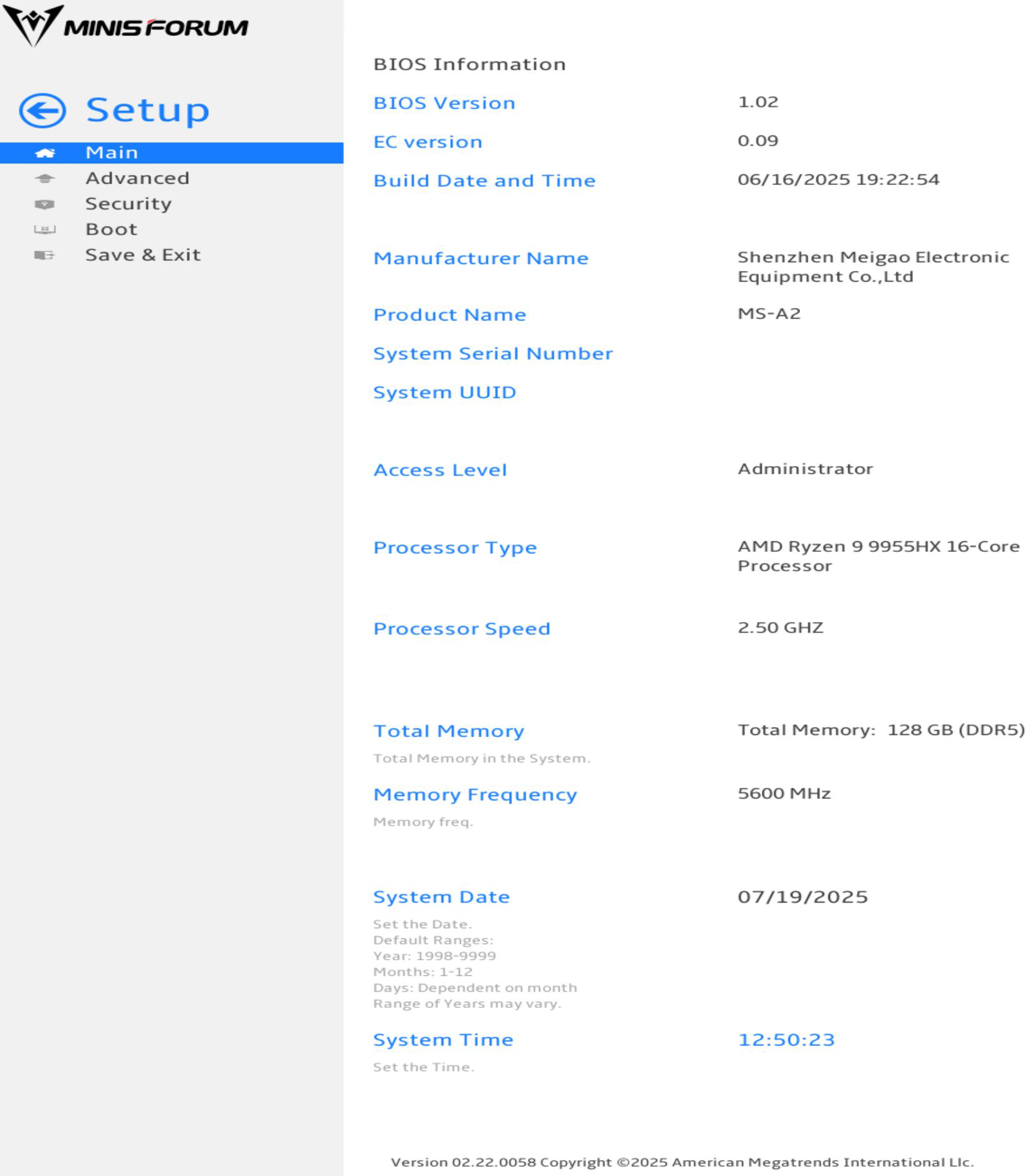
The BIOS that the Minisforum MS-A2 runs is AMI (American Megatrends International). My MS-A2 is the AMD Ryzen 9 9955HX version. The BIOS version I am running is 1.02.
You can download BIOS updates from Minisforum here.
In this post, I will share my documentation of each BIOS option I found on the Minisforum MS-A2.
Booting
When the Minisforum boots, you see the Minisforum splash screen.
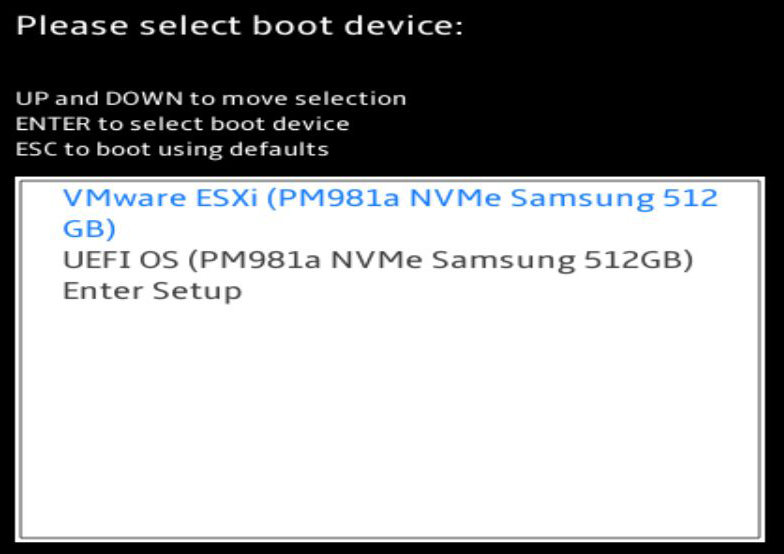
When the Minisforum is booting, you can press F7 to access the boot menu or press Del to enter the BIOS.
F7 Boot Menu Screen
Delete Menu Screen
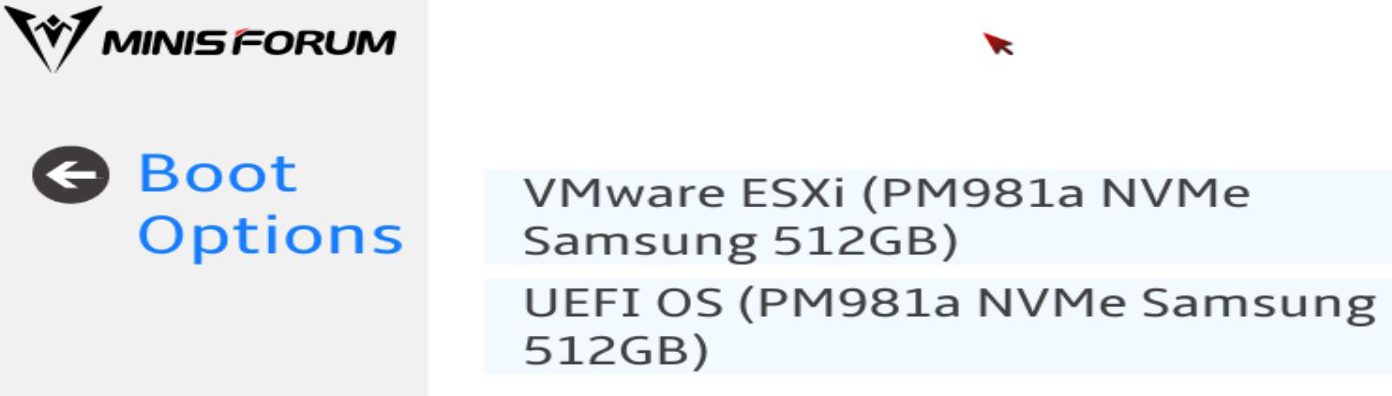
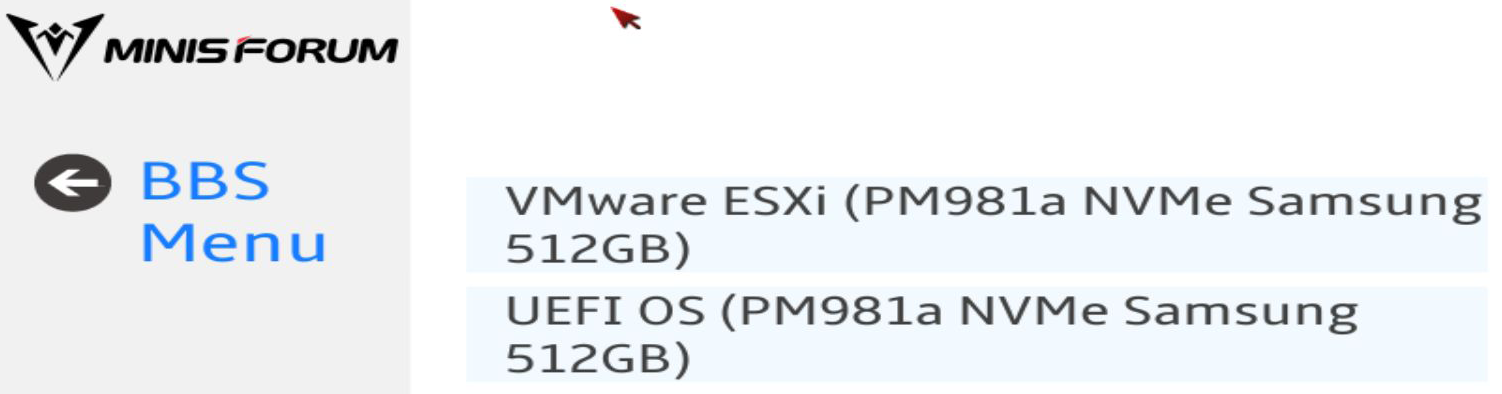
When you press Delete, you are presented with an initial menu that allows you to select several options, including Setup, Boot, UEFI Shell, Boot Options, and BBS Menu.
- Setup will take you into the BIOS.
- Boot will boot the system normally
- UEFI Shell tries to load shell.efi from any of the attached devices.
- Boot Options will bring up a menu to select a boot device.
- BBS Menu (BIOS Boot Spec) will also display a menu to select a boot device.
BIOS Setup
The BIOS Setup has the following menus.
Main
- For System Date, you can enter the date.