FotiGate Enable Policy Mode
The default setup of a Fortinet FortiGate is Profile mode. Here’s step-by-step how to change a FortiGate from Profile Mode to Policy Mode. Due to the significant change between the two mode you will need to rebuild all your rules.
Notes
- All existing firewall rules will be lost.
- Any objects or interfaces will remain.
- You will need to use Central NAT.
The Process
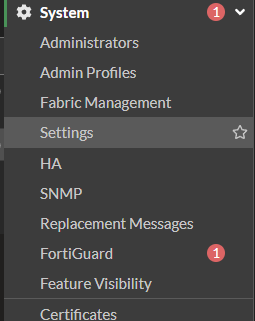
- Login to the FortiGate
- Click on System
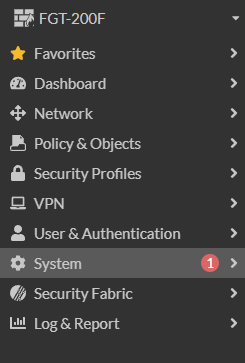
- Click on Settings