Saved Browser Passwords
It’s super convenient to save your passwords to your web browser but it isn’t very secure. In this post, I will show you step-by-step how to easily reveal a saved browser password.
Normally if you want to view a saved password you need to go into settings and click on it, then enter the password of the logged-in user account to view it. This isn’t always true, let me show you how to get around this.
The Process
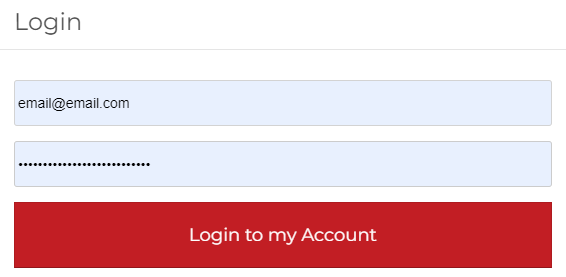
- Go to any website that has the login credentials saved.
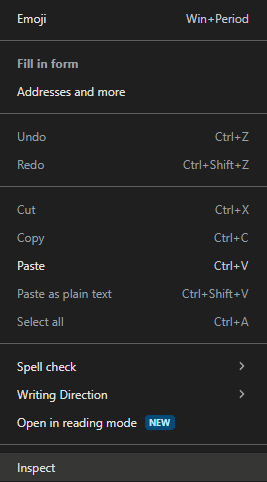
- Right-click on the password field and select inspect or just inspect the whole page.
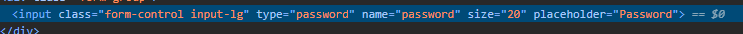
- Find the line for the password field this should show up as
type="password"