
Palo Alto User-ID and Terminal Server Agent Certificates
On November 18th, 2024, the certificates that the Palo Alto User-ID agent and the Palo Alto Terminal Server agent use to communicate with a Palo Alto firewall will expire, causing all communication to fail.
Palo Alto Networks has made new versions of the User-ID and TS agents with updated certificates that will expire on January 1st, 2032.
Before upgrading the User-ID or TS agent, you must upgrade your Palo Alto firewall to a version that supports the updated User-ID and TS agent certificate. Check the Palo Alto advisory here to determine which PAN-OS version you need.
If you want to know how to upgrade a Palo Alto firewall using CLI my blog post Upgrade Palo Alto HA Pair (Active/Passive) with CLI covers the entire process. If you want to upgrade your Palo Alto firewall using the GUI, my blog post, Upgrade Palo Alto Firewall HA Pair (Active/Passive), covers the entire process.
Once you’ve upgraded your Palo Alto firewall, you can upgrade the User-ID and TS agents to the new version.
My blog post, Palo Alto User-ID Agent Upgrade, details the entire upgrade process for the User-ID agent. My blog post, Palo Alto Terminal Server Agent Upgrade, details the upgrade process for the Terminal Server agent.
After I upgraded my User-ID and TS agents, I wanted to validate that everything was using the new certificates before the expiry deadline. I couldn’t find a straightforward way to check. However, I figured out a way.
In this post, I will detail step-by-step how to check the certificates that the Palo Alto User-ID agent and the Palo Alto Terminal Server agent use to communicate with PAN-OS.
The Process
- Connect to the system that has the Palo Alto User-ID or TS agent installed and browse to the installation directory.
User-ID is typically installed to C:\Program Files (x86)\Palo Alto Networks\User-ID Agent
TS Agent is typically installed to C:\Program Files\Palo Alto Networks\Terminal Server Agent
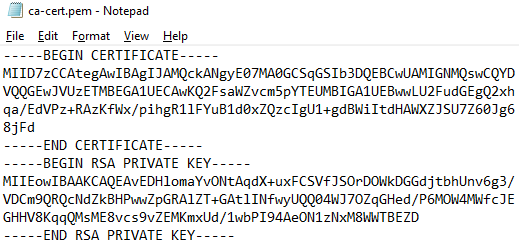
- Open the
ca-cert.pemfile with notepad.
- Copy the certificate to a certificate decoder.
I like to use CyberChef. Here’s the recipe I used.
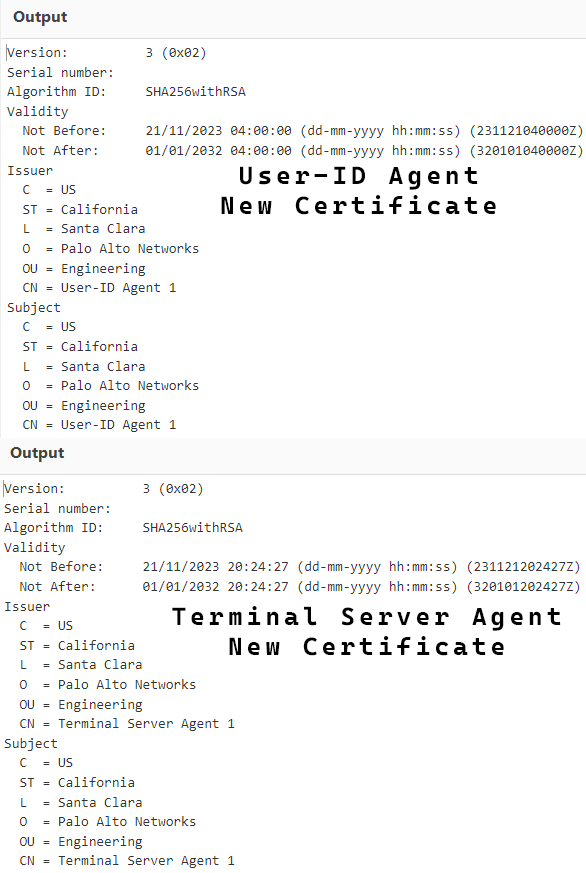
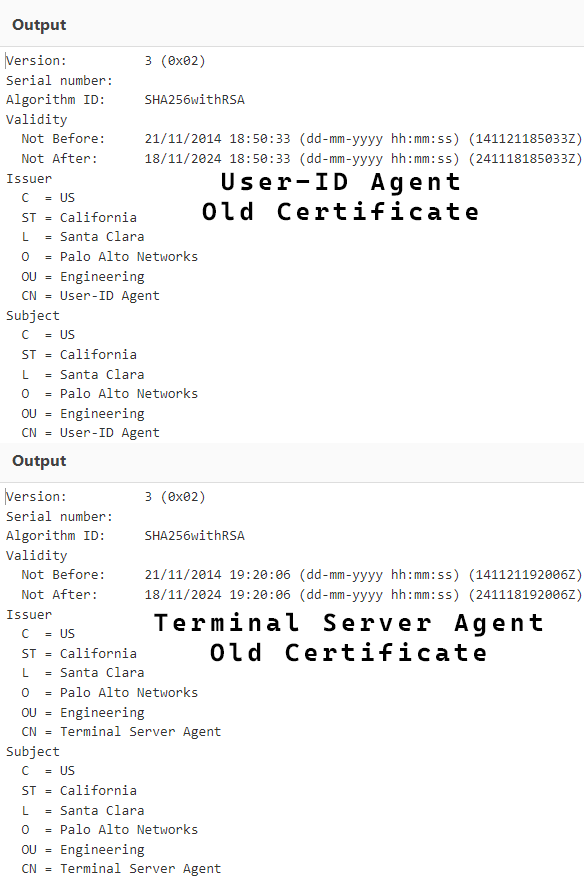
When you paste the certificate, you should get an output like this.
If the Not After date says 01/01/2032, you have already upgraded and are safe until 2032.
If the Not After date says 18/11/2024, you must upgrade your Palo Alto User-ID or TS Agent to get the new certificate.
That’s all it takes to check the certificate expiry date on the Palo Alto User-ID agent or the Palo Alto Terminal Server agent.




4 thoughts on “Palo Alto User-ID and Terminal Server Agent Certificates”
Hello,
I have 10.2-h4 do and I don’t have any USER ID agent only local users as administrators, do I need to upgrade palo alto version?
If you don’t use User-ID then you don’t need to upgrade to address the User-ID certificate expiry. However newer versions of other PAN-OS address other issues and you may want to upgrade to fix those issues. If you aren’t currently running a preferred release of PAN-OS I’d personally recommend looking into upgrading to a preferred release.
Hi , thanks por your explication , but is possible validate the information for certificated under de Palo alto via cli post upgrade Firewall and Agent id ?
Thanks
Hello,
I believe there is a way to validate the certificates using CLI using the Palo Alto User ID check https://github.com/PaloAltoNetworks/userid-check I haven’t tried that method.