
Entra Application Proxy
There are a few ways to grant external access to an internal application without doing any port forwarding. The way to do this in Microsoft’s world is through an Entra Application Proxy.
The name is a bit of a mess, as Microsoft renamed the Microsoft Entra application proxy program to Microsoft Entra private network connector. The Microsoft Entra private network connector is part of Microsoft Entra Private Access, which is part of Microsoft Global Secure Access.
Basically, Microsoft Entra Enterprise Applications can be configured with an Application Proxy, which will use the Microsoft Entra private network connector to proxy the connection.
In this post, I will show you step-by-step how to set up a Microsoft Entra private network connector, configure an internal web application to use an Entra Enterprise application proxy, and add authentication before access is granted to the web application.
Prerequisites
- Microsoft Entra ID P1 or higher license.
- External domain added to Microsoft 365.
- Windows Server for the Private Network Connector.
- Internal DNS name for the application.
- Access to the external DNS records.
- SSL certificate in PFX format with a password.
The Process
The process will be broken up into the following sections.
Private Network Connector
We need to set up the Entra private network connector as the Entra application proxy will proxy its connections via the private network connector.
- Log in to the Microsoft Entra Admin Center
- Click on Global Secure Access
If needed, click on Activate to Activate Global Secure Access for your tenant.
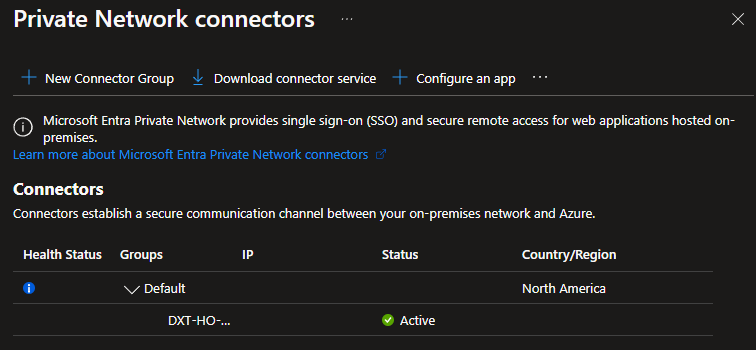
- Under Global Secure Access, click on Connect > Connectors.
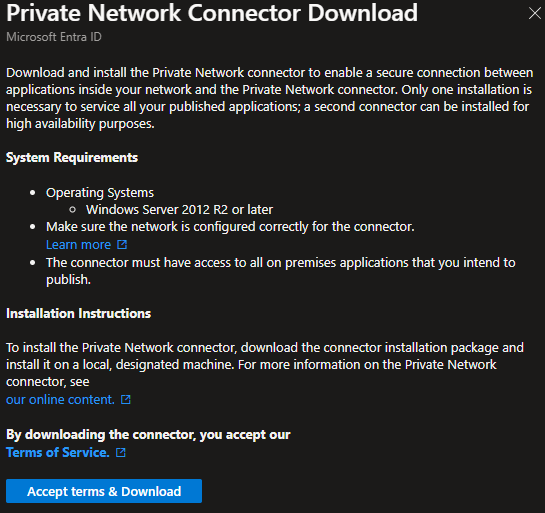
- Click on Download Connector service.
If your tenant says, “Private Network is currently disabled for your tenant” that’s fine, it will be enabled once the connector install is completed.
- Click on Accept terms & Download to start the download.
- Start installing the Microsoft Entra private network connector on the Windows Server you will use.
The Windows Server needs to be newer than Windows Server 2012 R2. You can put the server in a DMZ or on your regular network. The server will need access to everything you proxy through it. I’ve found that having the server domain joined yields the best results.
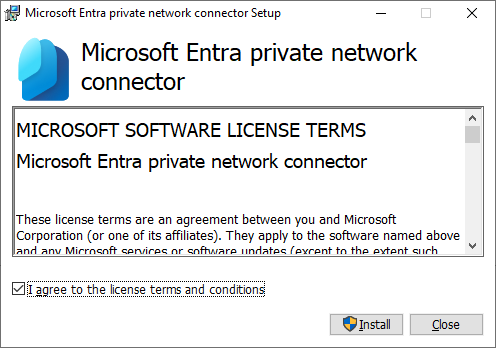
- Select I agree to the license terms and conditions and click Install.
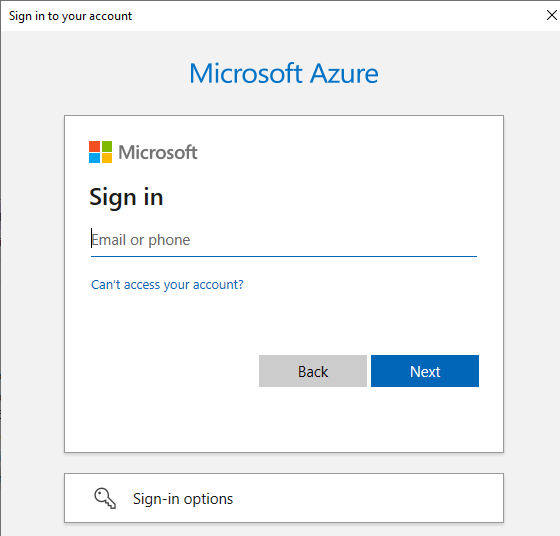
- When prompted, log in with a Microsoft 365 account to register the connector for your tenant.
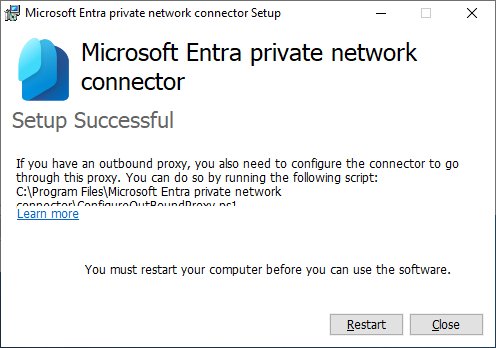
- Reboot if needed.
If you refresh the Private Network connectors screen, you should see the Microsoft Entra private network connector you installed.
Application Proxy
Now that we have the Entra Private network connector configured we can setup the Entra Application Proxy.
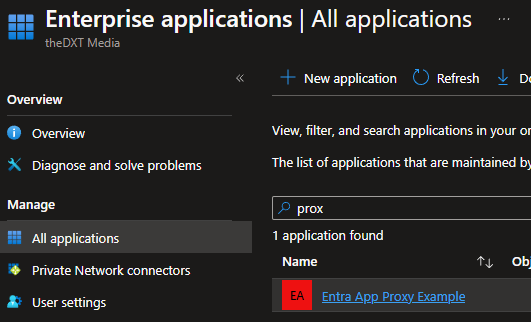
- Under Identity, click on Applications > Enterprise applications.
- Click on New application.
- Click on Add your own on-premises application.
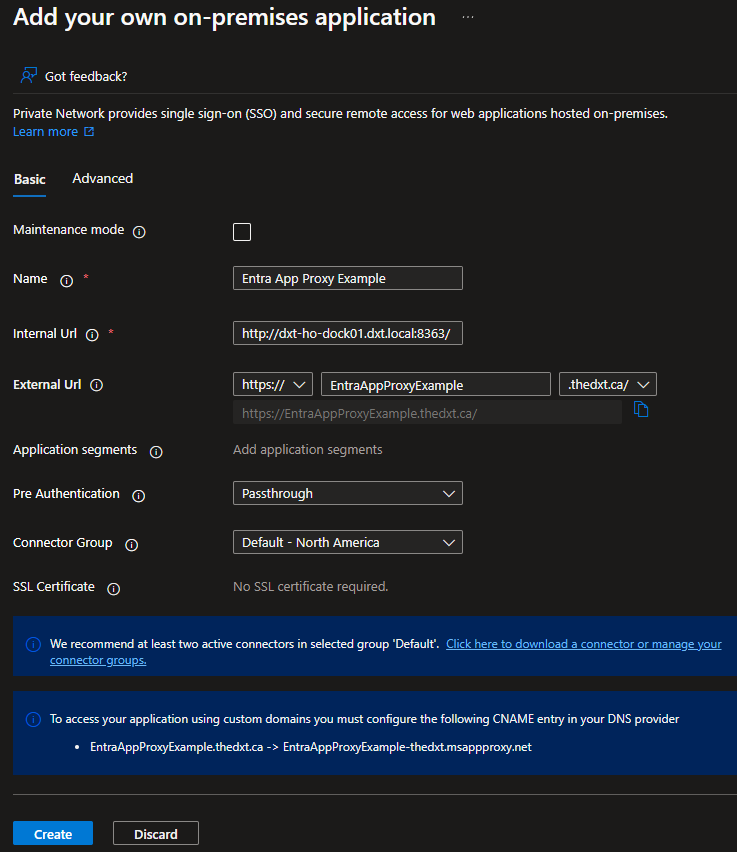
- Give the application a name.
For example, I will use the name Entra App Proxy Example.
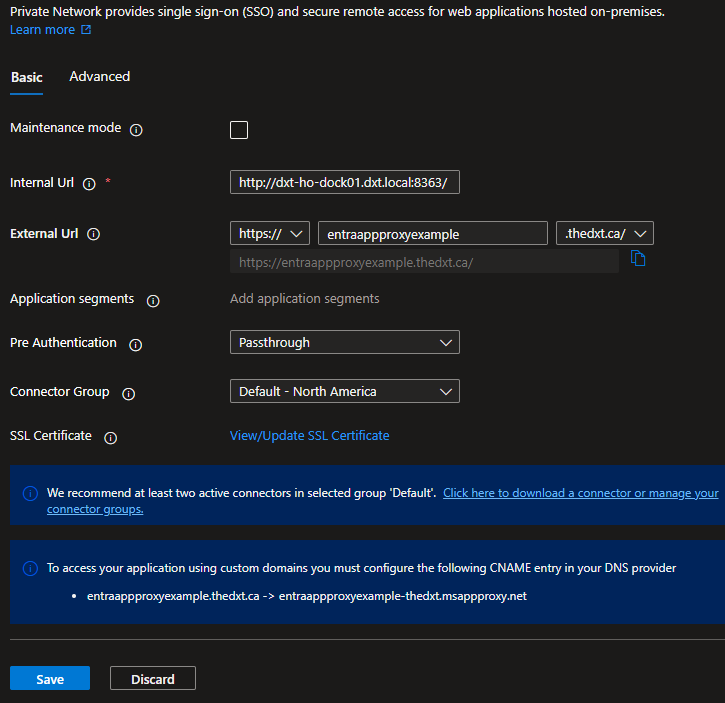
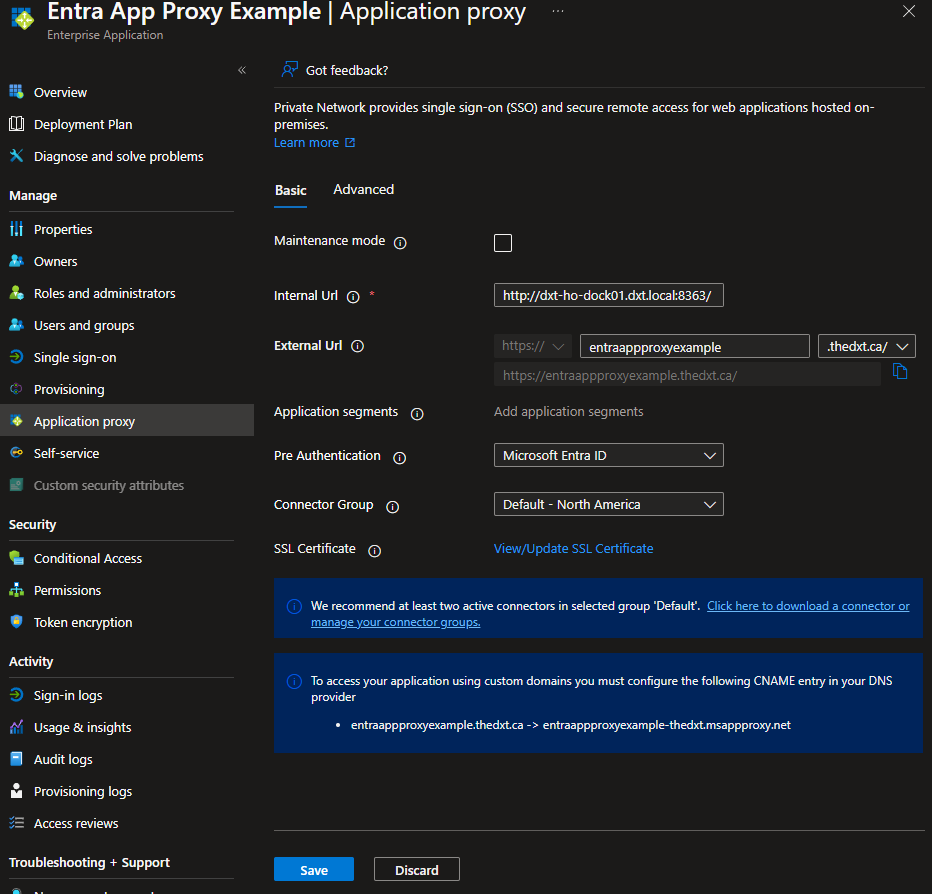
- Provide the internal URL for the application.
It can not be an IP address. But it can be a local DNS zone. The server running the private network connector will need to be able to resolve the DNS and will need access to the application.
For example, I will use dxt-ho-dock01.dxt.local, which runs a web application on port 8363.
- For the external URL, you can only select domains already in the Microsoft 365 tenant.
For example, I will use the domain thedxt.ca.
- For Pre Authentication, select Passthrough.
When you select passthrough, there is no extra authentication. (We’ll come back to this later in the Authentication section.)
- Select your connector group.
- Configure the required CNAME record in your external DNS provider.
- Click on Create to create the Entra enterprise application.
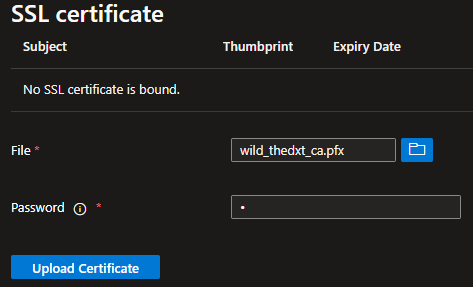
SSL Certificate
For some reason, you can’t add the SSL certificate when creating the application. We will add it now.
- Select the Entra Enterprise application that was just created.
- Click on Application proxy.
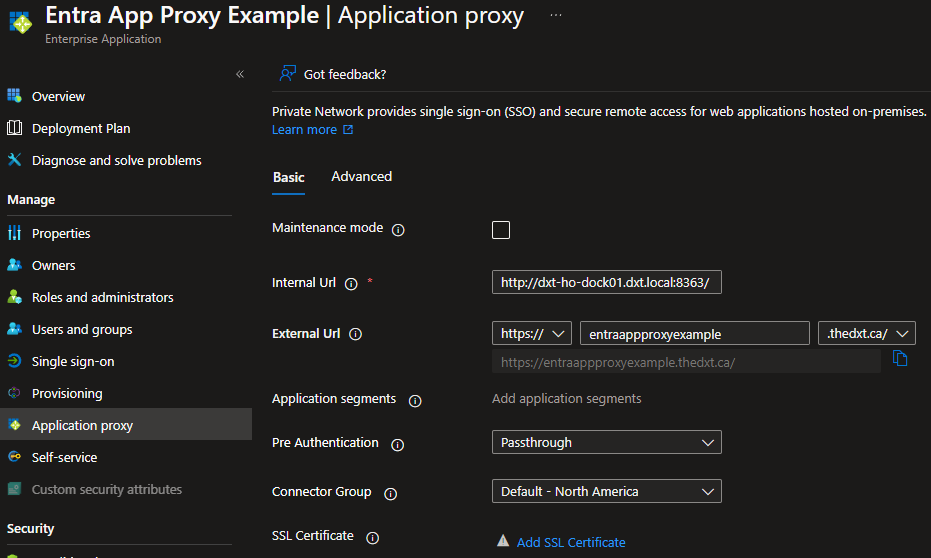
- Click on Add SSL Certificate.
- Upload the PFX of your SSL certificate, provide the PFX password and click Upload Certificate.
- Click Save to save the changes and start using the SSL certificate.
Testing
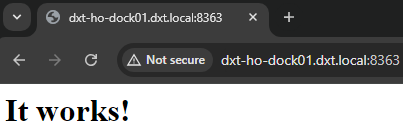
Here is what the web application looks like running internally.
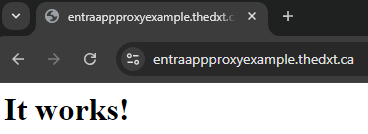
Using the Microsoft Entra private network connector and the Entra Enterprise application proxy, the web application can be accessed externally via entraappproxyexample.thedxt.ca.
Authentication
Now that we know the web application is working with the application proxy let’s add some authentication before you can access the application.
- Select the Entra Enterprise application we created.
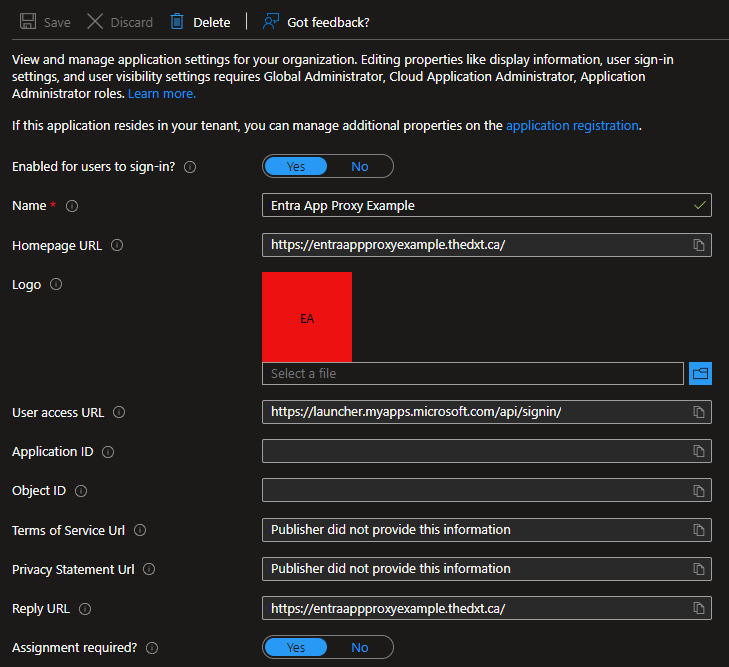
- Click on Properties.
- Confirm that Assignment required is set to Yes.
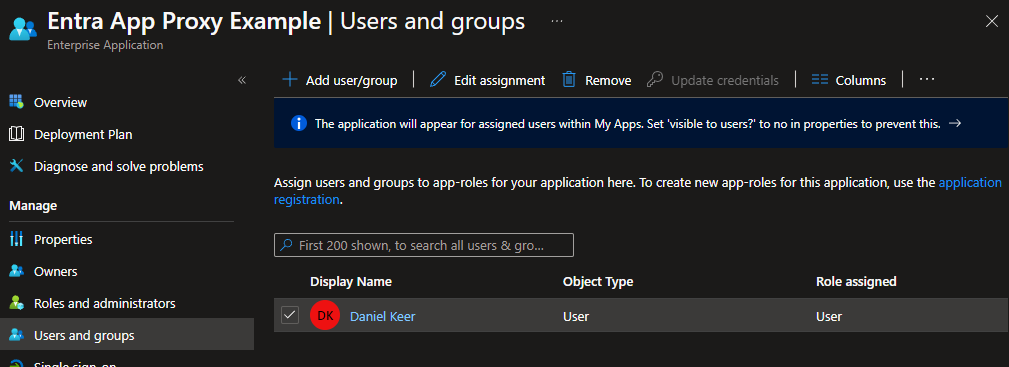
- Click on Users and groups and add the users and/or groups you want to allow access to the application.
- Click on Application proxy.
- For Pre Authentication, select Microsoft Entra ID and click Save.
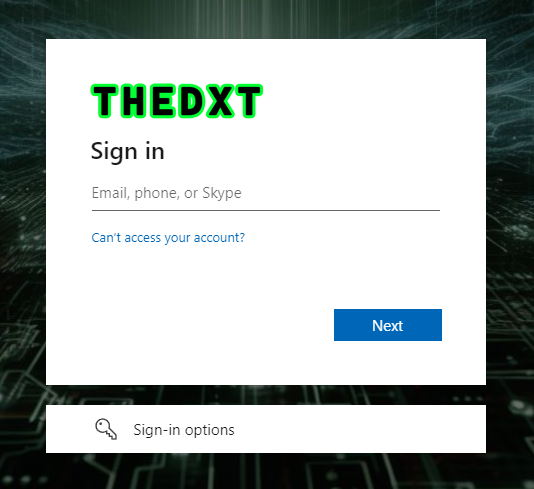
Now, when you try to access the application externally, you will need to log in with a Microsoft 365 account that has access before you can get to the application.
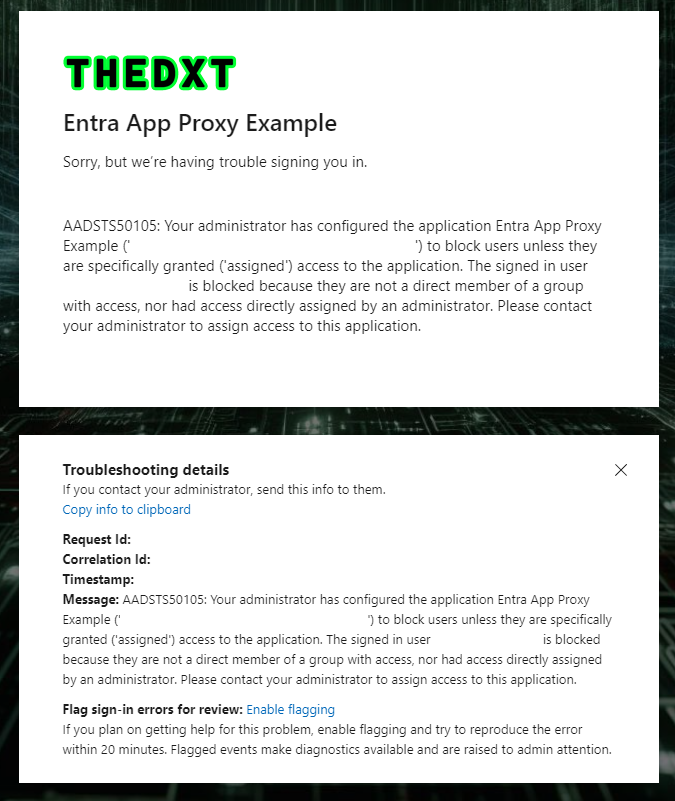
If the account doesn’t have access to the Entra Enterprise application, they will get an error message.
Summary
That’s all it takes to proxy an internal web application externally using the Microsoft Entra private network connector with an Entra Enterprise Application Proxy, including how to add authentication before access is allowed to the application.
Given that the Microsoft Entra application proxy is included with Entra ID P1 and higher plans, I’ve started using the Entra application proxy more as you are likely already paying for it.
If you want to read more about the Entra Application Proxy, here is the Microsoft documentation. If you want to read more about the Entra private network connector, here is the Microsoft documentation.




One thought on “Entra Application Proxy”