Entra ID External Authentication Methods with Duo
Microsoft recently introduced the public preview of External Authentication Methods in Microsoft Entra ID. I am very excited about External Authentication Methods as they finally allow third-party MFA providers like Cisco Duo to integrate better with Microsoft Entra ID (formerly Microsoft Azure AD).
Microsoft has supported third-party MFA providers for years. The original method for adding external MFA providers is Custom Controls, which was introduced in 2017 as a public preview.
As MFA grew in necessity, the limitations of Custom Controls became apparent. In 2020, Microsoft announced that Custom Controls would not leave public preview but a new solution that addressed its limitations would be created. In May of 2024, the replacement solution External Authentication Methods (EAM) was released as a public preview.
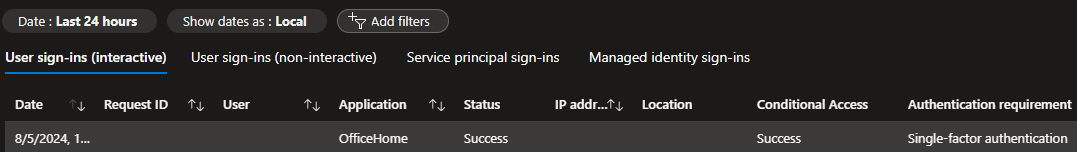
EAM addresses the limitations with Custom Controls, such as satisfying the Multifactor authentication requirement in a conditional access policy rather than using a custom control. EAM is a big deal, as the Entra sign-in logs show Custom Controls as a single-factor authentication when that is not true. I suspect this is because Microsoft has no way of validating whether MFA was completed or not.
Here’s an example of the Entra ID Sign-in logs with Duo using a Custom Control that reports as a Single-factor authentication.
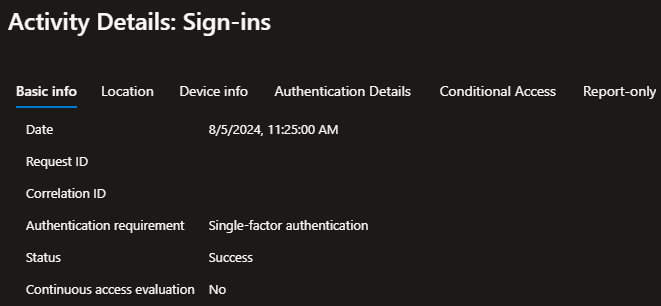
If we drill into more details under the Basic info tab, we will still see that the login is reporting as single-factor authentication.
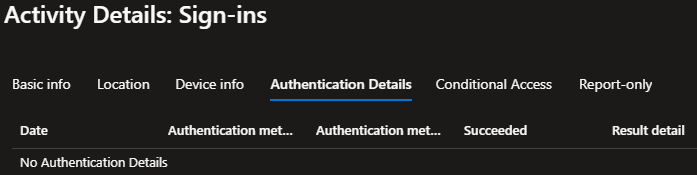
If we look at the Authentication Details tab, we will see nothing. I suspect this is because Entra has no way of knowing what happened on the Duo side of things, only that Duo said yup this user is good move along.
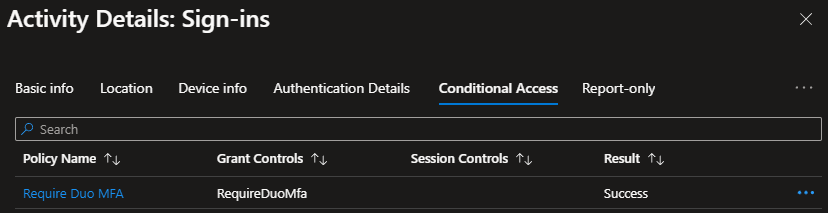
If we look at the Conditional Access tab, we finally see that Duo was applied with the custom control and that the result was a success.
The issue of Custom Controls reporting as single-factor authentication in the sign-in logs is resolved with EAM.
Using EAM, we can now directly use third-party MFA solutions like Cisco Duo as an MFA option in Microsoft Entra Authentication methods, allowing us to use the MFA setting in a conditional access policy instead of a custom control. This even allows you to be more granular with the accepted forms of MFA, such as allowing Windows Hello rather than just Duo to grant MFA.
External Authentication Methods is currently in preview. However, everything seems to be working correctly in my testing.
In this post, I will show you step-by-step how to set up Cisco Duo with External Authentication Methods in Microsoft Entra ID.
The Process
Initial Setup
- Login to the Duo Admin console.
- Click on Applications > Protect an Application
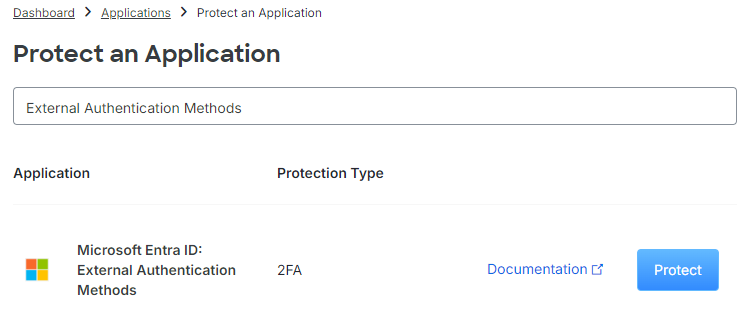
- Search for External Authentication Methods and click on Protect beside Microsoft Entra ID: External Authentication Methods.
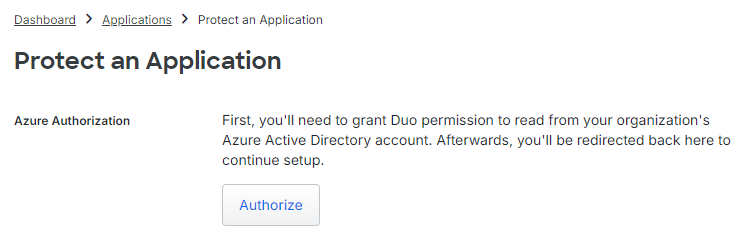
- Click on Authorize to spawn the process for Duo to create the needed Enterprise application in your Microsoft 365 tenant.
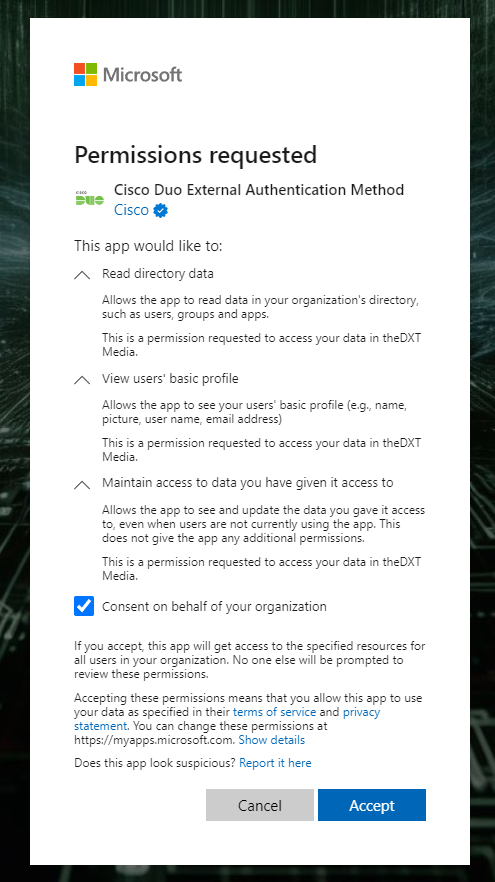
You will see the permissions requested screen for the Cisco Duo External Authentication Method application.
- Select Consent on behalf of your organization and click Accept.
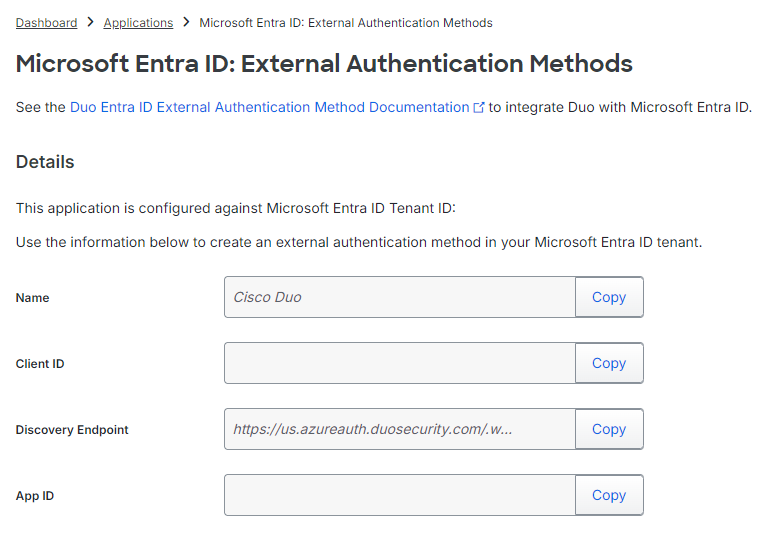
- Note the Client ID, Discovery Endpoint, and App ID.
- Log in to the Microsoft Entra Admin Center
- Click on Protection > Authentication methods
- Click on Add external method.
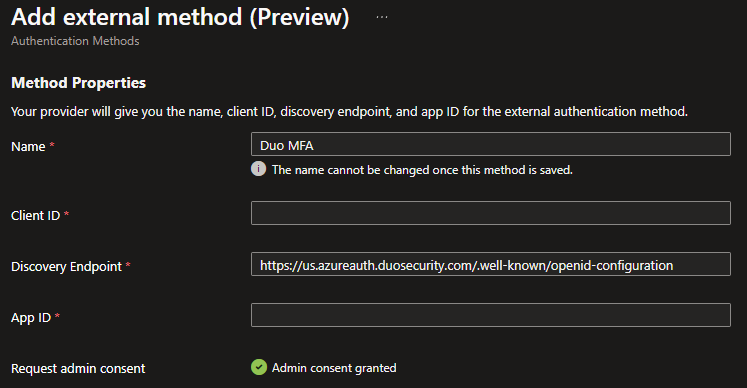
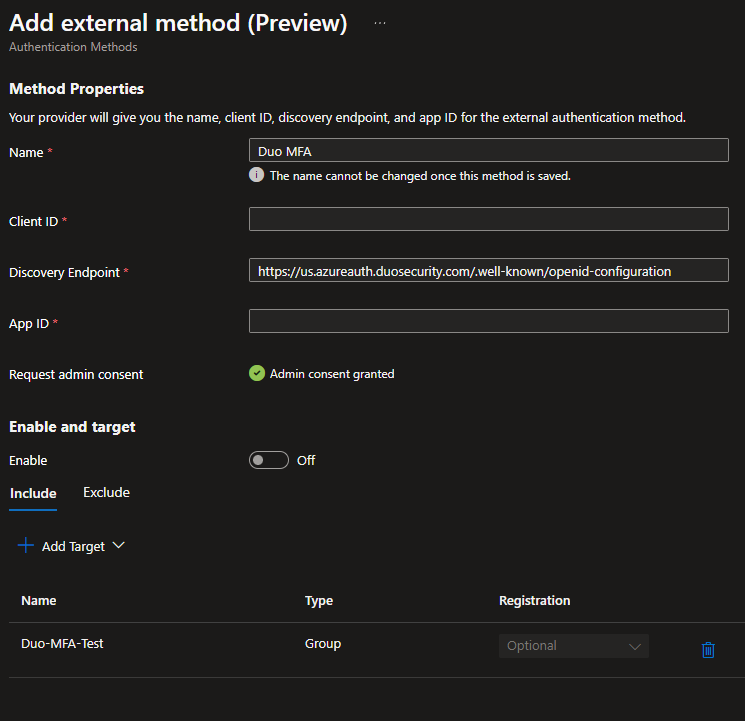
- Enter a name for the authentication method.
Once you’ve selected a name, you can not change it. The name you enter will also be shown to users. I will be using the name Duo MFA.
- Enter the Client ID, Discovery Endpoint, and App ID you noted from Duo.
- Select the groups you want to allow the Duo external authentication method.
I will be using a group named Duo-MFA-Test.
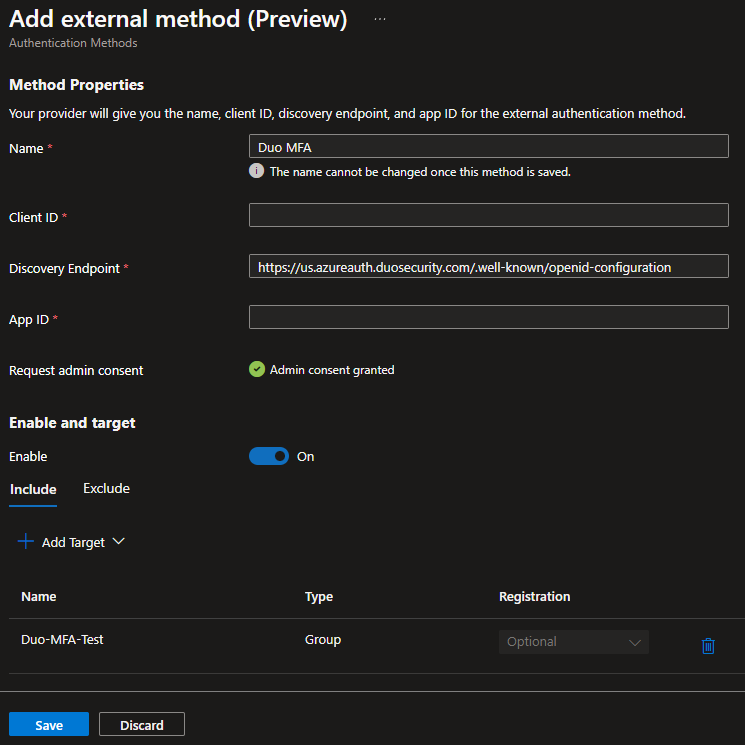
- Set Enable to On and click Save.
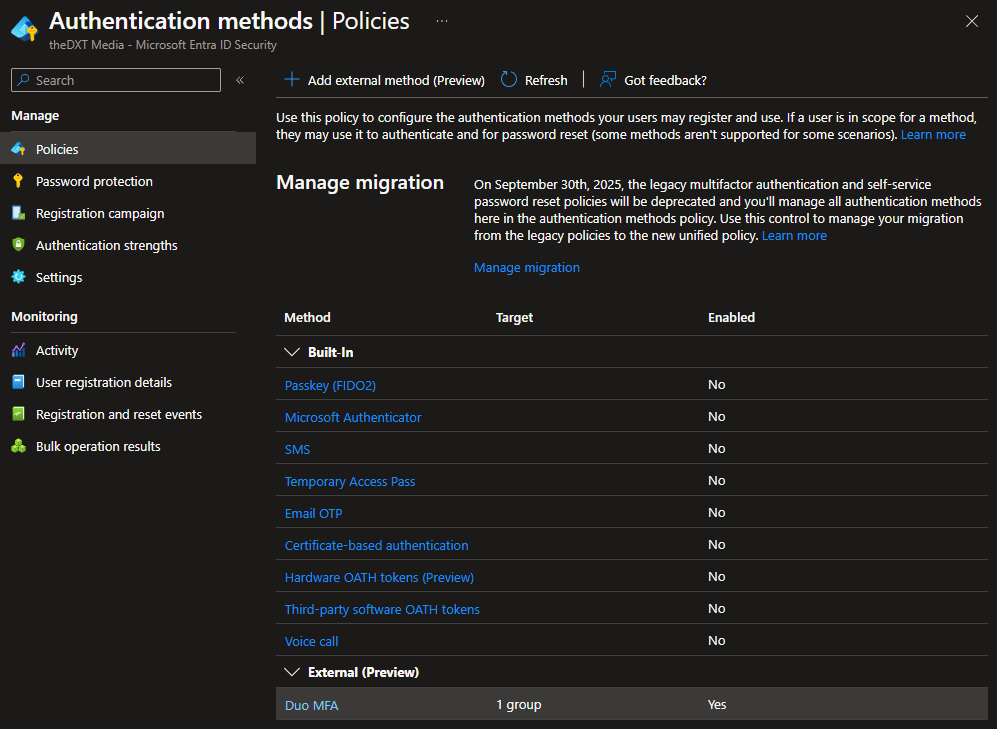
You will now see the external authentication method you just created.
Configure Conditional Access Policy
Now that the initial setup is completed, we need to configure a Conditional Access policy to use the Duo external authentication method.
- Click on Protection > Conditional Access.
- Click on Create new policy.
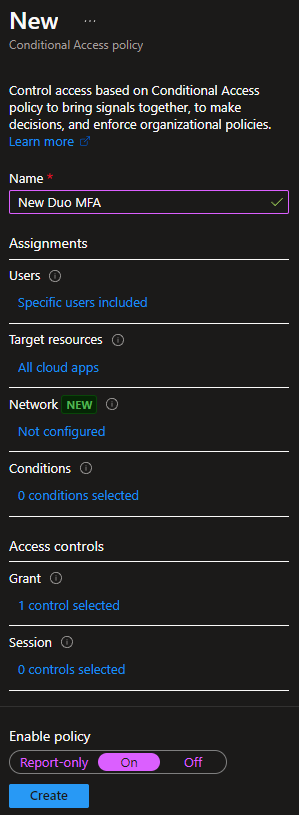
- Give your new Conditional Access policy a name. I will use the name New Duo MFA.
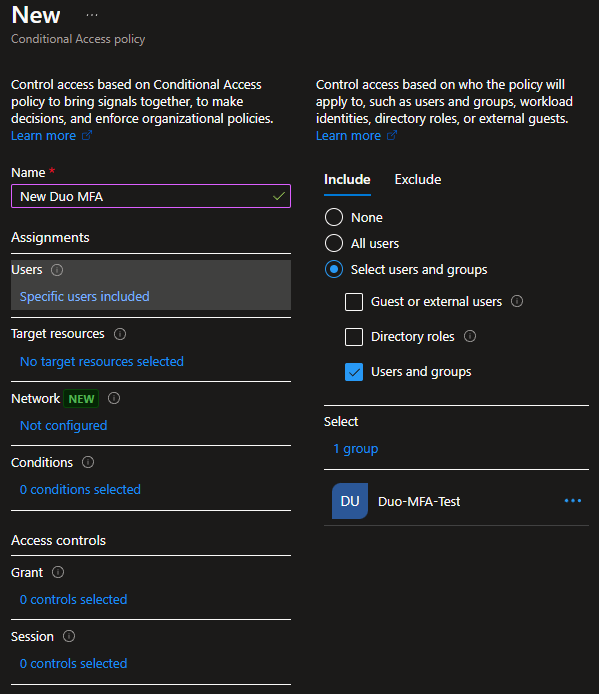
- Under Assignments, select the users you want the policy to target.
In my example, I will use the group named Duo-MFA-Test.
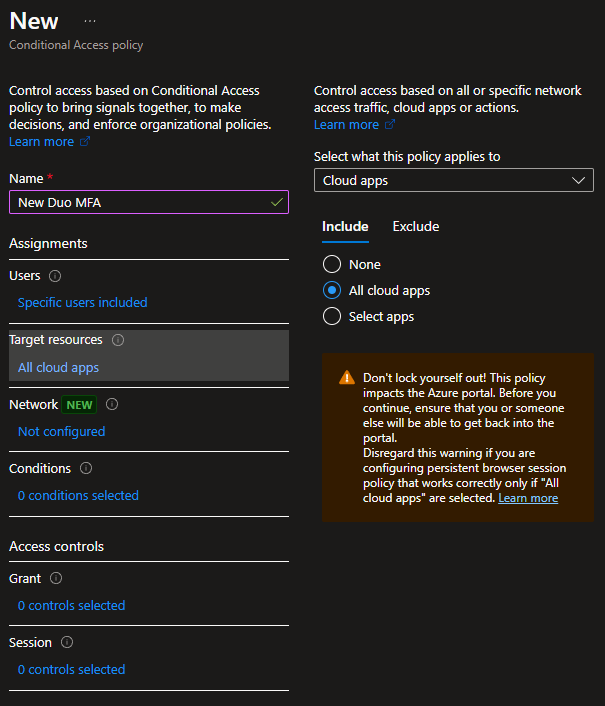
- Under Assignments, select the resources you want to target.
In my example, I will target all cloud apps. If you aren’t taking a phased approach to the Conditional Access policy, you may want to select the Office 365 app to help prevent locking yourself out if something doesn’t work correctly.
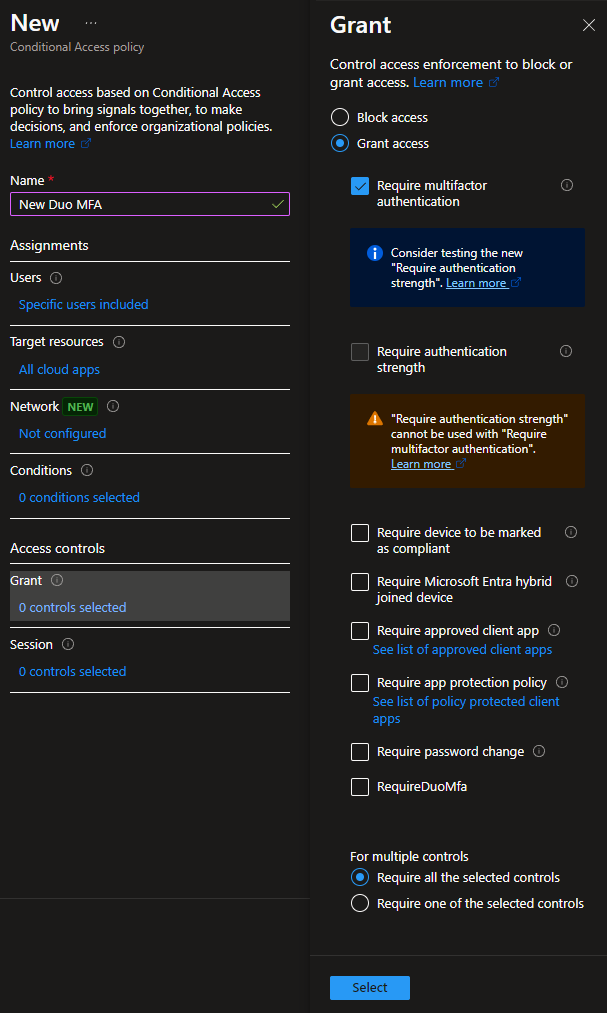
- Under Access controls, select Grant to configure the grant access method and select Require multifactor authentication.
We don’t need to select the RequireDuoMfa grant as that is the original Duo grant that uses a custom control, and we are replacing it with EAM.
- Set Enable policy to On and click Create.
Testing
Now that the conditional access policy has been created, we can test it.
- Login to Microsoft 365.
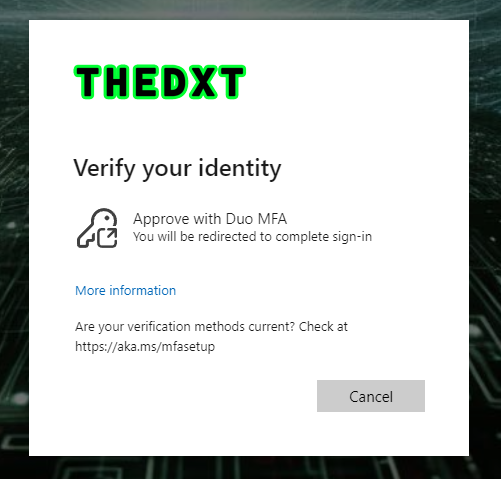
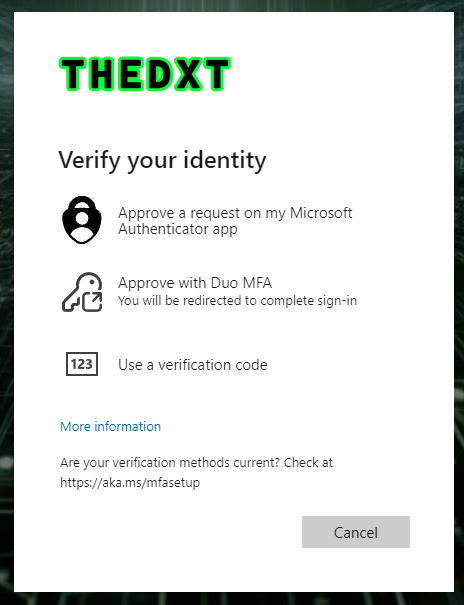
After a successful password, we see a new screen asking us to approve our login with Duo.
- Click on Approve with Duo MFA.
The approve with name the user sees is the name you entered when you added the External Authentication Method.
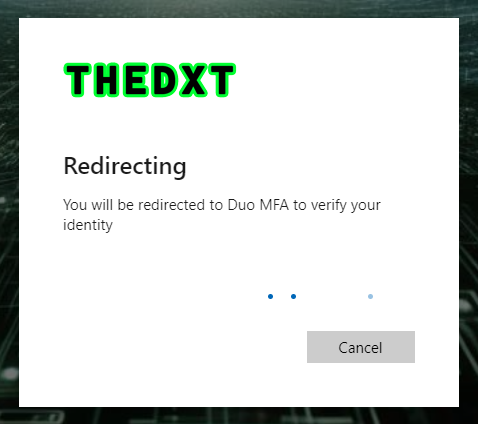
The user will briefly see a screen informing them they are being redirected to Duo to verify their identity.
- Approve the login with Duo.
- You are now logged in to Microsoft 365 and approved the login with Duo using EAM.
That’s all it takes to configure Microsoft Entra ID to use External Authentication Methods with Cisco Duo.
Logs
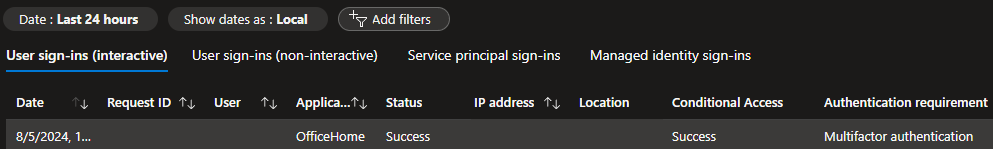
If we look at the Entra sign-in logs, we will see that Duo now shows up as a Multifactor authentication.
Here’s an example of the Entra ID Sign-in logs with Duo EAM.
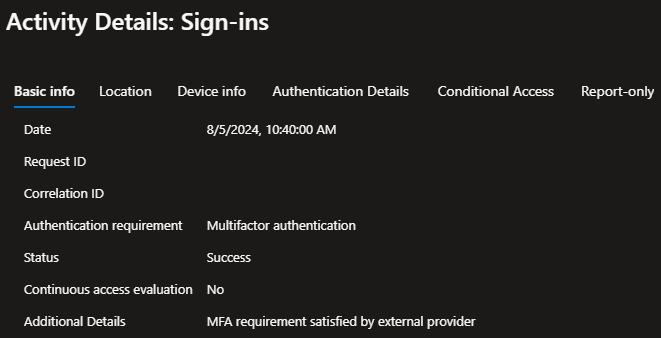
The Basic info tab shows that Multifactor authentication was successful, and an external provider was used.
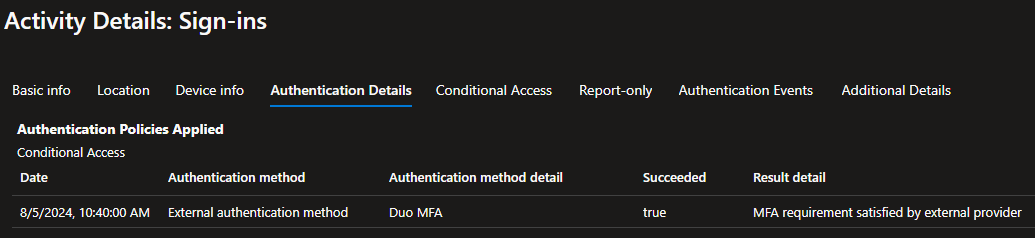
If we look at the Authentication Details tab, we will see that the authentication method is an external authentication method and that the method is Duo and Duo completed the MFA.
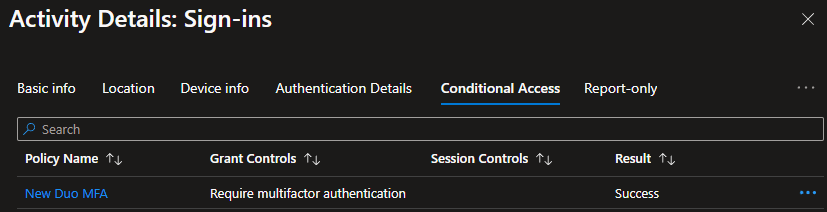
On the Conditional Access tab we can see that the conditional access policy we created, New Duo MFA, used the Grant Control Require multifactor authentication and was successful.
Extras
If the user has multiple authentication methods, they can select their preferred MFA method. The options a user sees can be controlled with the require authentication strength setting however, at this time, external methods can’t be defined in authentication strengths.
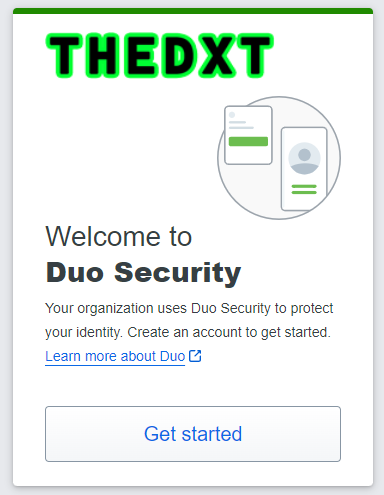
If a user doesn’t have Duo set up for their account, when they select Approve with Duo, they will be guided through the setup of Duo.
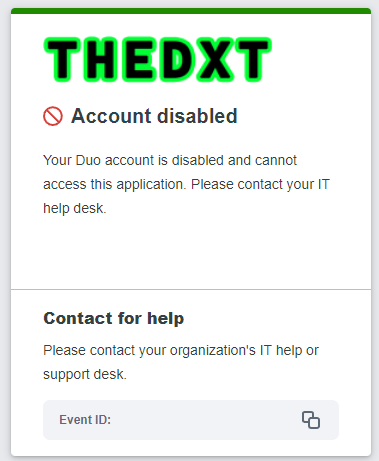
If a user is disabled in Duo, they will get an error from Duo after selecting the Duo EAM.
If a user is set to Bypass in Duo, they will get an error message from Duo after selecting the Duo External Authentication Method.
External authentication methods doesn’t fully support everything yet, like self-service password resets, but it’s for sure a step in the right direction.
If you want to read more about configuring Duo with Entra ID External Authentication Methods, here is the Duo documentation.
If you want to read more about the External Authentication Methods in Microsoft Entra ID, here is the Microsoft documentation.