
Certificate Chain
This post will explain the main components of a certificate and how they contribute to a certificate chain.
A certificate chain consists of three main components:
- A root CA (Certificate Authority) certificate.
- One or more intermediate CA (Certificate Authority) certificates.
- A server certificate.
Root CA
A root CA is the most trusted source of authority for certificates. It is the first link in a certificate chain, and all certificates are issued by it in one way or another.
There are two main types of root CAs. The first is an internal root CA, which is common on corporate networks, and the second is a public root CA.
Technically speaking, a root CA is just a CA with a self-signed certificate. What sets a public root CA apart is that their self-signed certificates are widely pre-loaded by operating systems and web browsers, making them trusted by default.
This is the list of the public root CAs trusted by Chromium based web browsers, and this is the list of the public root CAs trusted by Microsoft Windows.
Because public root CAs are widely pre-trusted, when you install a TLS/SSL certificate issued by a public root CA on a web server or web application, you don’t need to do anything else to make your certificate trusted.
Internal root CAs are more commonly seen on corporate networks, as IT typically controls the devices on a corporate network, and IT will have some level of automation pre-installing the root CA certificate on all devices to make them trust the internal root CA.
Root CAs are commonly left offline or on an air-gapped network to reduce the risk of a root CA becoming compromised.
Intermediate CA
The intermediate CA, sometimes called a subordinate CA, is the next link in the certificate chain after the root CA.
An intermediate CA will have a certificate issued by a root CA. Because the root CA is trusted, the intermediate CA is also trusted, and certificates issued by an intermediate CA will also be trusted.
An intermediate CA’s primary purpose is to issue certificates more broadly on behalf of a root CA, removing the need for a root CA to issue certificates directly and providing some degree of separation.
In some situations, there can be more than one intermediate CA adding more links in the certificate chain, each trusting the previous one and so on.
Server Certificate
After one or more intermediate CAs, your certificate, also known as a client or server certificate, is the final link in the certificate chain.
An intermediate CA will issue the server certificate. Because the intermediate CA is trusted, any certificates it issues are also trusted, which is why your certificate is trusted. A server certificate can not issue certificates.
If you look back at the certificate chain, you can see how everything is directly related to the item above it or below it.
- The root CA is widely trusted, and all certificates issued by the root CA are also trusted.
- The intermediate CA has a certificate issued by the root CA, which makes the intermediate CA trusted, and all certificates issued by the intermediate CA are trusted.
- The server certificate is trusted because it is issued by an intermediate CA that is trusted.
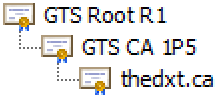
My website, thedxt.ca, has a server certificate for thedxt.ca, issued by the intermediate CA GTS CA 1P5. The intermediate CA GTS CA 1P5 certificate is issued by the public root CA GTS Root R1. Because GTS Root R1 is a public root CA that your web browser trusts, you can visit my website without any certificate errors.
The image above is an example of a certificate chain. Each item is issued by the previous one, and because the root CA is trusted, the entire chain is trusted.
It used to be common practice to issue a server certificate with an expiry that spanned several years. However, on September 1, 2020, Apple decided to make a change across their systems, making it so that Apple devices will only trust a certificate for a maximum of 398 days. As a result, everyone was forced to adopt this change, which is why we need to replace public-facing certificates once a year.
Summary
All certificates are issued by a root CA in some way. An intermediate CA is allowed to issue certificates on behalf of a root CA and has a certificate issued by a root CA. A server certificate can not issue certificates and has a certificate issued by an intermediate CA. Each certificate is issued by the one above it, and this forms the certificate chain. Because the root CA is trusted, the whole chain is trusted.




3 thoughts on “Certificate Chain”